How to Integrate Sudoers with OpenLDAP Server
Sudo is an application that allows you to get root or administrator privileges on Linux and Unix operating systems. Sudo is mostly installed by default on Linux distributions, also you can set up user authorization via the /etc/sudoers file and enable unprivileged users to execute specific commands as the root user.
Sudo can be configured in multiple ways, you can set up sudo on a local computer/server or you can also set up a centralized sudo via third-party software. And for this example, you will be using the OpenLDAP server to set up centralized sudo deployment.
In this tutorial, we will set up and integrate sudoers to the OpenLDAP server. With this, you will have a centralized user and sudo privileges management on your OpenLDAP server allowing the installation on the client side faster. Any SSSD service on the client machine configured with a sudo authentication source allows OpenLDAP users to execute sudo.
Prerequisites
You must ensure that you have the following requirements to complete this guide:
- A server with OpenLDAP Server installed and configured.
- A client machine OpenLDAP Client and SSSD service configured.
- If you're using RHEL-based Distributions, ensure that the SELinux is running in Permissive mode.
This example will be using two machines for the OpenLDAP Server and Client. Both machines are running the Rocky Linux 9 server. Below is the detailed servers:
Hostname IP Address Used as Domain/FQDN
--------------------------------------------------------------
ldap 192.168.5.25 OpenLDAP Server ldap.hwdomain.lan
client 192.168.5.80 OpenLDAP Client client.hwdomain.lan
Import Sudoers Schema to OpenLDAP Server
In the first step, you must import default sudoers LDAP schema to your OpenLDAP servers. This can be done via the LDIF file and the 'ldapadd' utility.
Log in to the OpenLDAP server and copy the default sudoers schema for LDAP by entering the cp command below.
sudo cp /usr/share/doc/sudo/schema.OpenLDAP /etc/openldap/schema/sudo.schema
Next, enter the following nano command editor command to create a new LDIF file '/etc/openldap/schema/sudo.ldif'.
sudo nano /etc/openldap/schema/sudo.ldif
Add the following lines to the file.
dn: cn=sudo,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: sudo
olcAttributeTypes: ( 1.3.6.1.4.1.15953.9.1.1 NAME 'sudoUser' DESC 'User(s) who may run sudo' EQUALITY caseExactIA5Match SUBSTR caseExactIA5SubstringsMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 )
olcAttributeTypes: ( 1.3.6.1.4.1.15953.9.1.2 NAME 'sudoHost' DESC 'Host(s) who may run sudo' EQUALITY caseExactIA5Match SUBSTR caseExactIA5SubstringsMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 )
olcAttributeTypes: ( 1.3.6.1.4.1.15953.9.1.3 NAME 'sudoCommand' DESC 'Command(s) to be executed by sudo' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 )
olcAttributeTypes: ( 1.3.6.1.4.1.15953.9.1.4 NAME 'sudoRunAs' DESC 'User(s) impersonated by sudo (deprecated)' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 )
olcAttributeTypes: ( 1.3.6.1.4.1.15953.9.1.5 NAME 'sudoOption' DESC 'Options(s) followed by sudo' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 )
olcAttributeTypes: ( 1.3.6.1.4.1.15953.9.1.6 NAME 'sudoRunAsUser' DESC 'User(s) impersonated by sudo' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 )
olcAttributeTypes: ( 1.3.6.1.4.1.15953.9.1.7 NAME 'sudoRunAsGroup' DESC 'Group(s) impersonated by sudo' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 )
olcObjectClasses: ( 1.3.6.1.4.1.15953.9.2.1 NAME 'sudoRole' SUP top STRUCTURAL DESC 'Sudoer Entries' MUST ( cn ) MAY ( sudoUser $ sudoHost $ sudoCommand $ sudoRunAs $ sudoRunAsUser $ sudoRunAsGroup $ sudoOption $ description ) )
Save and exit the file when you're done.
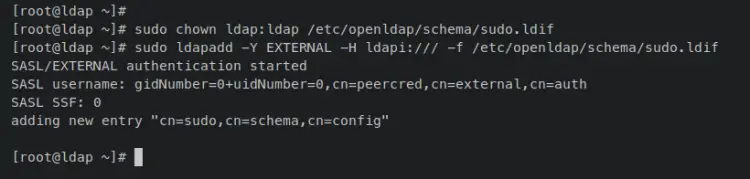
Change the ownership of the sudoers LDIF file '/etc/openldap/schema/sudo.ldif' to ensure that the OpenLDAP can access it.
sudo chown ldap:ldap /etc/openldap/schema/sudo.ldif
Now enter the following 'ldapadd' command to add the sudoers LDAP schema to the OpenLDAP server. With this, you will add the new 'cn' called 'sudo' to the OpenLDAP server and allow any OpenLDAP users within the 'cn=sudo' to execute the sudo command on client machines.
sudo ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/sudo.ldif
When successful, you should get an output such as 'adding new entry "cn=sudo,cn=schema,ch=config"'.
Now that the sudoers LDAP schema added, you will need to set up an 'ou' or Organizational Unit for the sudoers.
Creating Organization Unit for Sudo
After adding the sudoers LDAP schema, you will next create a new 'ou' or Organizational Unit called 'sudo' that allows any OpenLDAP users within this ou to execute the sudo command. Also, you will set up the default sudoers configuration for OpenLDAP users.
Enter the following nano editor to create a new file 'sudoers.ldif'.
sudo nano sudoers.ldif
Add the following lines to the file and be sure to change the main domain with your OpenLDAP server domain name.
# sudoers.ldif
dn: ou=sudo,dc=hwdomain,dc=lan
objectClass: organizationalUnit
objectClass: top
ou: sudo
description: Default ou for SUDO
Save and close the file when finished.
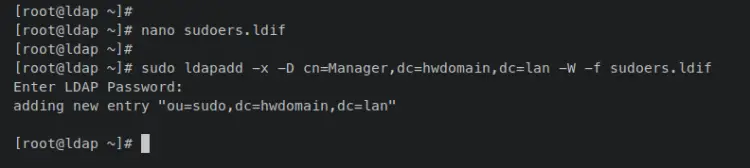
Next, enter the following 'ldapadd' command to add the sudoers ou to the OpenLDAP server. When prompted for a password, input the correct OpenLDAP root password.
sudo ldapadd -x -D cn=Manager,dc=hwdomain,dc=lan -W -f sudoers.ldif
When the operation is successful, you should receive an output such as 'adding new entry "ou=sudo,dc=hwdomain,dc=lan"'.
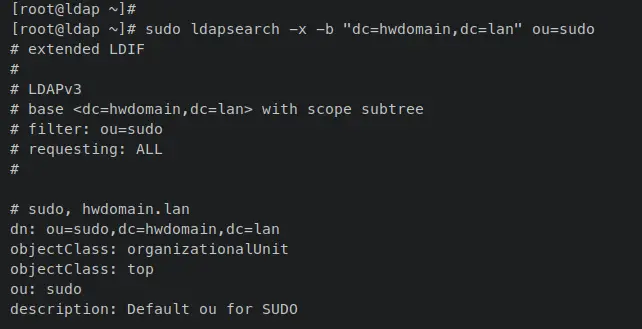
Now enter the following 'ldapsearch' command to find any 'ou' with the value 'sudo' on the OpenLDAP server.
sudo ldapsearch -x -b "dc=hwdomain,dc=lan" ou=sudo
The output below confirms that the 'ou=sudo' added and is available on the OpenLDAP Server.
Next, create another LDIF file that will define the default sudoers configuration. Enter the following nano editor command to create a new file 'sudoconf.ldif'.
sudo nano sudoconf.ldif
Add the following lines to the file.
# sudoconf.ldif
dn: cn=defaults,ou=sudo,dc=hwdomain,dc=lan
objectClass: sudoRole
objectClass: top
cn: defaults
sudoOption: env_reset
sudoOption: mail_badpass
sudoOption: secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
#sudoOrder: 1
Save and close the file when finished.
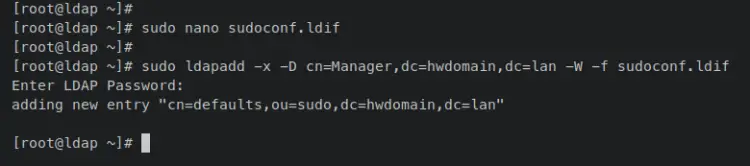
Now enter the 'ldapadd' command below to add the default sudoers configuration to the OpenLDAP Server. Any OpenLDAP users within the 'ou=sudo' will apply the default sudoers configuration.
sudo ldapadd -x -D cn=Manager,dc=hwdomain,dc=lan -W -f sudoconf.ldif
Input your OpenLDAP root password when prompted. When successful, you have an output like this:
With this, the configuration of sudoers on the OpenLDAP server is finished. You can now add OpenLDAP users to the 'ou=sudo', which allowed OpenLDAP users to execute the sudo command.
Adding OpenLDAP Users to Sudo
In this section, you will learn how to add OpenLDAP to the 'ou=sudo' to allow users to execute the 'sudo' command on OpenLDAP client machines. With this, you add an existing OpenLDAP user to the 'ou=sudo' or add a new user with the 'ou=sudo'.
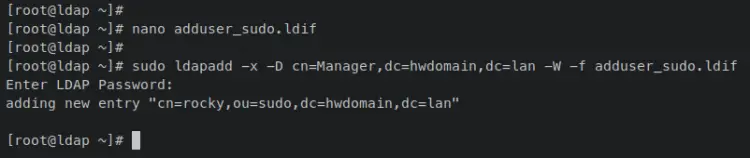
Create a new LDIF file 'adduser_sudo.ldif' using the following nano editor command.
nano adduser_sudo.ldif
Add the following lines to the file. This will add an existing OpenLDAP user 'rocky' to the 'ou=sudo' and allow the user 'rocky' to execute the 'sudo' command on client machines. Also, be sure to change the domain name 'dc=hwdomain,dc=lan' with your OpenLDAP server domain.
# adduser_sudo.ldif
dn: cn=rocky,ou=sudo,dc=hwdomain,dc=lan
objectClass: sudoRole
objectClass: top
cn: rocky
sudoCommand: ALL
sudoHost: ALL
sudoRunAsUser: ALL
sudoUser: rocky
Save and close the file when finished.
If you want to create a new OpenLDAP user with the default 'ou=sudo', use the following LDIF file and be sure to change the parameter of 'userPassword', username, and default domain name for your OpenLDAP server.
# adduser.ldif
dn: uid=rocky,ou=People,dc=hwdomain,dc=lan
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
cn: rocky
sn: temp
userPassword: {SSHA}cDG5NuQd+rYn6rWh1r5UnysUOwJlt1uk
loginShell: /bin/bash
uidNumber: 2000
gidNumber: 2000
homeDirectory: /home/rocky
shadowLastChange: 0
shadowMax: 0
shadowWarning: 0
dn: cn=rocky,ou=Group,dc=hwdomain,dc=lan
objectClass: posixGroup
cn: rocky
gidNumber: 2000
memberUid: rocky
dn: cn=rocky,ou=sudo,dc=hwdomain,dc=lan
objectClass: sudoRole
objectClass: top
cn: rocky
sudoCommand: ALL
sudoHost: ALL
sudoRunAsUser: ALL
sudoUser: rocky
Next, enter the following 'ldapadd' command below to apply the changes to OpenLDAP servers. When prompted, input your OpenLDAP server password.
sudo ldapadd -x -D cn=Manager,dc=hwdomain,dc=lan -W -f adduser_sudo.ldif
When successful, you should receive an output such as 'adding new entry "cn=rocky,ou=sudo,dc=hwdomain,dc=lan"'.
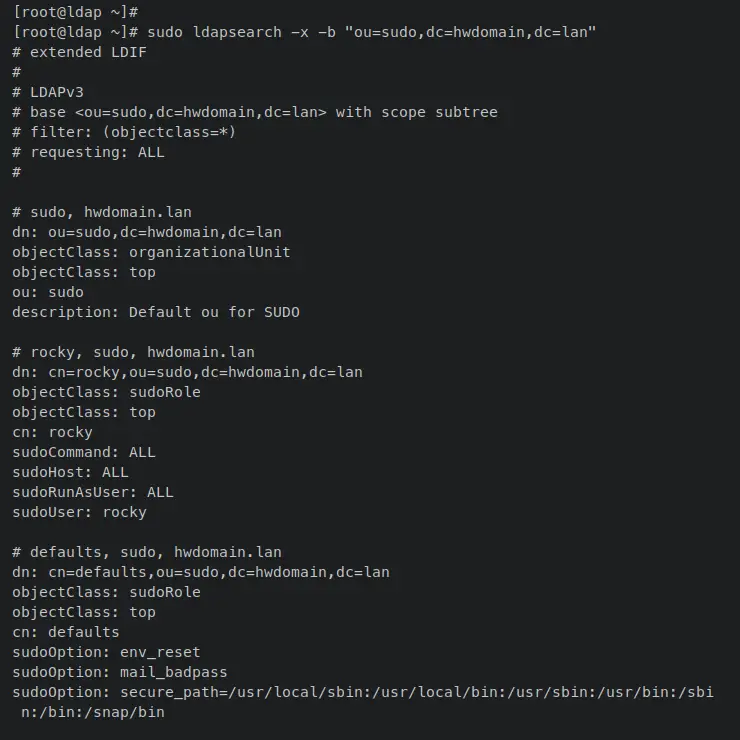
Lastly, enter the following 'ldapsearch' command to show and verify the list of users on the 'ou=sudo'. With this, you should see your new user added and available on the 'ou=sudo'.
sudo ldapsearch -x -b "ou=sudo,dc=hwdomain,dc=lan"
At this point, you have now added an existing OpenLDAP user called 'rocky' to the 'ou=sudo' and allows the user to execute the 'sudo' command on client machines.
In the next step, you will add new settings to the SSSD service to enable the sudoers over the OpenLDAP server.
Setting up OpenLDAP Client Machine
On the client machine, you must add some settings to the nsswitch and sssd configurations. Be sure to run the following commands on the OpenLDAP client machine.
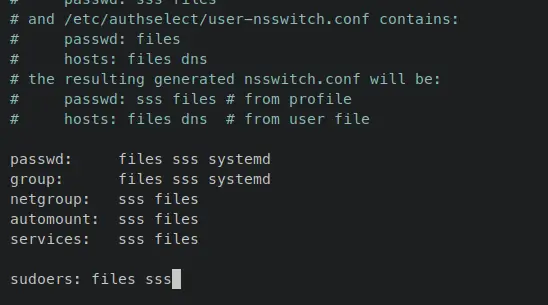
On the Nsswitch config file '/etc/nsswitch.conf', you should define the sudoers name service to allow sudoers management via the SSSD service. Then, on the SSSD config file '/etc/sssd/sssd.conf', you must add the 'sudo_provider' of the 'ldap', define the 'sudo' service, then add '[sudo]' section for additional sudoers configuration.
Open the Nsswitch config file '/etc/nsswitch.conf' using the following nano editor command.
sudo nano /etc/nsswitch.conf
Add the following configuration to define the 'sudoers' name service and allow it for management via the SSSD service.
sudoers: files sss
Save and close the file when finished.
Next, enter the following nano editor command to open the SSSD config file '/etc/sssd/sssd.conf'.
sudo nano /etc/sssd/sssd.conf
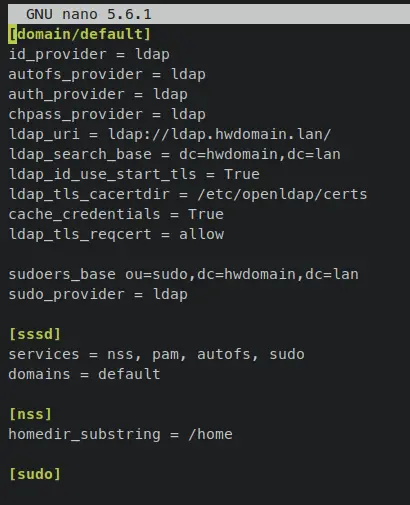
On the '[domain/default]' section, add new parameters 'sudoers_base' and 'sudo_provider. On the '[sssd]' section, you must add the 'sudo' on the 'services' parameter. If you need additional sudoers configuration, add the '[sudo]' section to the bottom of the line.
[domain/default]
....
sudoers_base ou=sudo,dc=hwdomain,dc=lan
sudo_provider = ldap
[sssd]
services = nss, pam, autofs, sudo
domains = default
[nss]
homedir_substring = /home
[sudo]
Save and close the file when you're done.
Lastly, enter the following systemctl command to restart the SSSD service and apply the changes.
sudo systemctl restart sssd
With the SSSD service restarted, the sudoers management via the OpenLDAP server is now enabled. Any OpenLDAP users that logged in to the default ou for sudo can execute the 'sudo' command on the client machine.
Verify Sudoers Integration with OpenLDAP Server
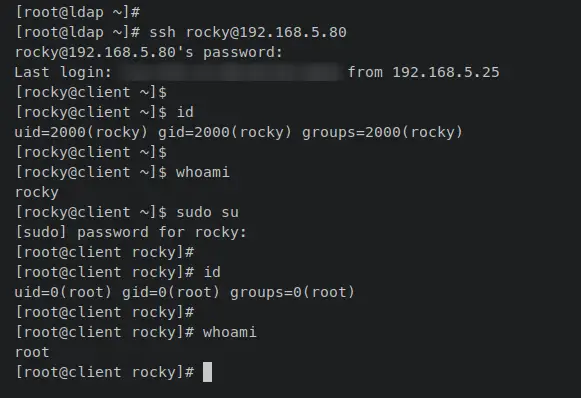
From the OpenLDAP server, log in to the client machine on IP address '192.168.5.80' with the OpenLDAP user 'rocky' via the 'ssh' command below.
ssh [email protected]
When prompted, input the password for the password. When successful, you should be logged in to the OpenLDAP client machine.
Enter the following commands to verify the current used user, gid, and uid. You should receive an output that the OpenLDAP user 'rocky' with gid and uid '2000'.
id
whoami
Lastly, enter the following 'sudo su' command to verify the sudoers' integration with the OpenLDAP server.
sudo su
When prompted, input the password for the user 'rocky'. When successful, your terminal prompt will become 'root@client ....'.
Now rerun the following command to verify the current user that you're using and you should see the current user is 'root'.
id
whoami
This confirms that the sudoers integration with the OpenLDAP server is finished and successful.
Conclusion
In this tutorial, you have configured and integrated sudoers with the OpenLDAP server that allows OpenLDAP users to execute the 'sudo' command on client machines. You have also integrated sudoers with SSSD service on client machines that will automatically enable sudo for OpenLDAP users.
With this, you can now add more OpenLDAP users to the 'ou=sudo' to allow users for executing sudo on the client machine. Also, you must update the configuration of nsswitch and SSSD on the client machines so the OpenLDAP users can connect to the OpenLDAP sudo providers.
To get more details about OpenLDAP checks OpenLDAP's official documentation. And for Sudoers, visit the sudoers' documentation.