How to Install InfluxDB and Telegraf on Debian 11
InfluxDB is an open-source time series database written in Go. It is a high-performance time series platform with purpose-built to collect, store, process, and visualize time series data. InfluxDB is the go-to solution for time series databases, it provides a high-performance time series data engine with built-in powerful API for building real-time applications. InfluxDB is a platform that is used for such as operation monitoring, application and server performance metrics, IoT sensor data, and real-time analytics.
In this guide, you will set up dashboard monitoring with InfluxDB and send metrics for system monitoring via Telegraf. You'll use a Debian 11 server for the installation. This guide includes how to secure InfluxDB via TLS/SSL certificates, set up InfluxDB via IbnfluxDB-CLI (Command Line), and basic Telegraf configuration for sending metrics to InfluxDB.
Prerequisites
To complete this guide, you will need the following requirements:
- A Debian 11 server - You can use two or three different servers for the installation. Below is the basic architecture when you are using multiple servers:
- server1 used as InfluxDB server.
- server2 as target monitoring where Telegraf will be installed.
- A non-root user with sudo/root administrator privileges.
Installing InfluxDB and InfluxDB-CLIs
InfluxDB is an open-source time series database that can be deployed in multiple environments, which includes virtual machines with Linux, Windows, and macOS. And also containerized environments such as Docker and Kubernetes.
The influxdb2-cli provides a command-line 'influx' that allows you to manage influxdb administration such as managing buckets, organizations, users, tasks, etc.
In this first step, you will set up the influxdb repository, then install influxdb and influxdb-cli packages to your system.
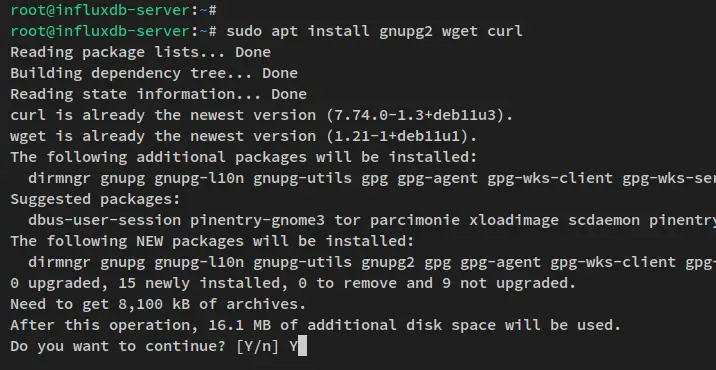
To start, run the below apt command to install some package dependencies to your Debian server. When prompted for the installation, input y and press ENTER.
sudo apt install gnupg2 wget curl
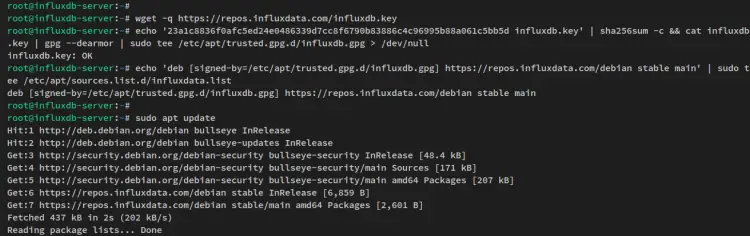
Next, run the below command to download the GPG key for the influxdb repository. The GPG key will be stored at '/etc/apt/trusted.gpg.d/influxdb.gpg'.
wget -q https://repos.influxdata.com/influxdb.key
echo '23a1c8836f0afc5ed24e0486339d7cc8f6790b83886c4c96995b88a061c5bb5d influxdb.key' | sha256sum -c && cat influxdb.key | gpg --dearmor | sudo tee /etc/apt/trusted.gpg.d/influxdb.gpg > /dev/null
Now add the influxdb repository to your system via the below command. In this example, you will install influxdb from the stable branch repository.
echo 'deb [signed-by=/etc/apt/trusted.gpg.d/influxdb.gpg] https://repos.influxdata.com/debian stable main' | sudo tee /etc/apt/sources.list.d/influxdata.list
After that, update and refresh your package index via the apt command below.
sudo apt update
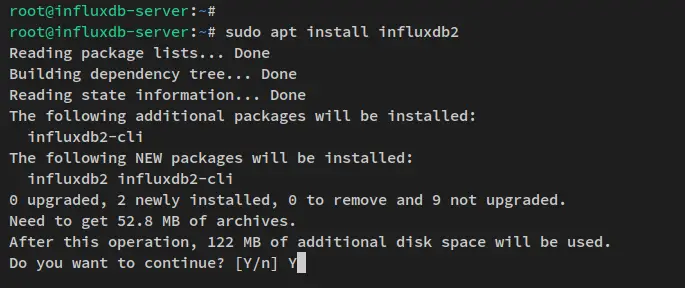
After the repository is added and the package index updated, run the apt command below to install the influxdb2 and influxdb2-cli packages. At the time of this writing, the latest stable version of influxdb is v2.xx and the influxdb-cli is v2.xx.
sudo apt install influxdb2 influxdb2-cli
When prompted for the configuration, input y and press ENTER to proceed.
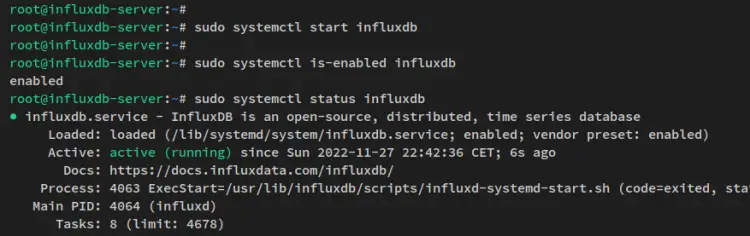
After influxdb2 and influxdb2-cli is installed, use the systemctl uitility command below to start the influxdb service.
sudo systemctl start influxdb
Lastly, verify the influxdb service using the systemctl utility command below.
sudo systemctl is-enabled influxdb
sudo systemctl status influxdb
You should receive the output of the influxdb service is enabled and will be run automatically upon the bootup. And the status of the influxdb service is running.
With the influxdb service running, you can proceed with the basic configuration of influxdb2-cli.
Configuring InfluxDB-CLI
The influxdb2-cli provides a command-line tool for managing the influxdb server - named 'influx'. You'll now verify the influxdb2-cli and set up the bash-completion for the 'influx' command.
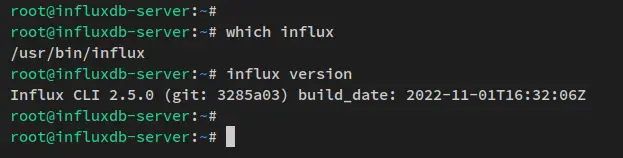
To verify the influxdb2-cli, run the below command on your terminal. The first command will check the full binary path of the 'influx' command, and the second command will verify the version of influxdb2-cli that is installed on your system.
which influx
influx version
You will receive the output like the following screenshot - the 'influx' command is available at '/bin/influx' and the version of the influxdb2-cli package that was installed is v2.xx.
Next, you'll set up the bash-completion for the 'influx' command via the '~/.bashrc' configuration file.
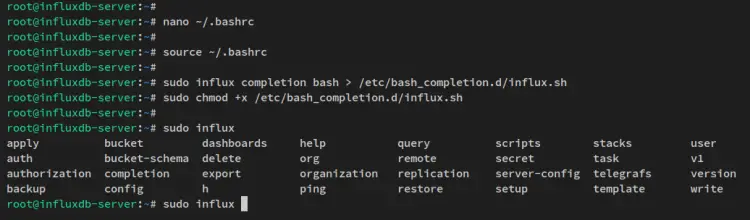
Run the influx command below to generate the bash-completion script to '/etc/bash_completion.d/influx.sh'. Then, make the newly generated script '/etc/bash_completion.d/influx.sh' executable via the chmod command.
sudo influx completion bash > /etc/bash_completion.d/influx.sh
sudo chmod +x /etc/bash_completion.d/influx.sh
Next, open the '~/.bashrc' configuration file via the following nano editor command.
sudo nano ~/.bashrc
Add the following configuration to the bottom of the line. With this, you will load bash script completion that is available on multiple directories.
# enable programmable completion features (you don't need to enable
# this, if it's already enabled in /etc/bash.bashrc and /etc/profile
# sources /etc/bash.bashrc).
if ! shopt -oq posix; then
if [ -f /usr/share/bash-completion/bash_completion ]; then
. /usr/share/bash-completion/bash_completion
elif [ -f /etc/bash_completion ]; then
. /etc/bash_completion
fi
fi
Save the file and exit the editor when you are finished.
Next, run the below command to reload the '~/.bashrc' configuration and reload your current shell.
source ~/.bashrc
Lastly, type the 'influx' command on your terminal and press TAB to get available options for the 'influx' command.
sudo influx TAB
You will then receive the output like the following.
Now that the influxdb service is running and the influxdb2-cli command-line is configured, you'll then set up the firewalld and start configuring the influxdb via the command-line influxdb2-cli.
Setting up UFW
The default influxdb service is running on port 8086. This port is also used as an end-point where influxdb will receive metrics from the telegraf.
In this step, you will set up the ufw firewall and open the influxdb port '8086' on the ufw firewall.
The ufw package isn't installed on the default Debian installation. Install ufw via the apt command below.
sudo apt install ufw -y
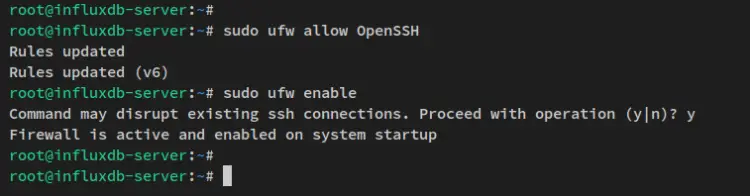
After the ufw package is installed, run the ufw command below to add the OpenSSH service and enabled the ufw firewall service.
sudo ufw allow OpenSSH
sudo ufw enable
When prompted for confirmation, input y and press ENTER. The ufw service should now be started and enabled and will be run automatically upon the bootup.
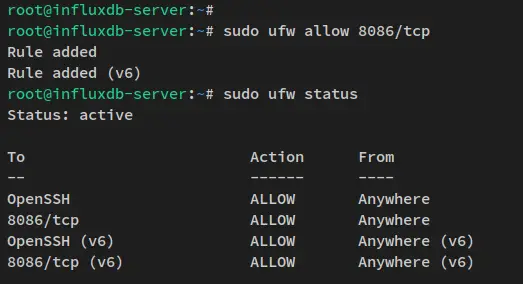
Next, run the below command to add port '8086' to the ufw firewall. Then, verify the current status of ufw firewall.
sudo ufw allow 8086/tcp
sudo ufw status
You'll receive the output like the following screenshot - The ufw firewall status is active with the enabled service OpenSSH and port '8086'.
Setting up InfluxDB via InfluxDB-CLI
To use the influxdb, you must configure it via web-based administration or using the influxdb2-cli command line. The basic configuration for influxdb includes the following:
- Influxdb admin user
- Influxdb admin password
- Default organization name
- Default bucket/database
In this step, you will set up the influxdb via the influx command provided by the influxdb2-cli package. Run the below command to start configuring influxdb.
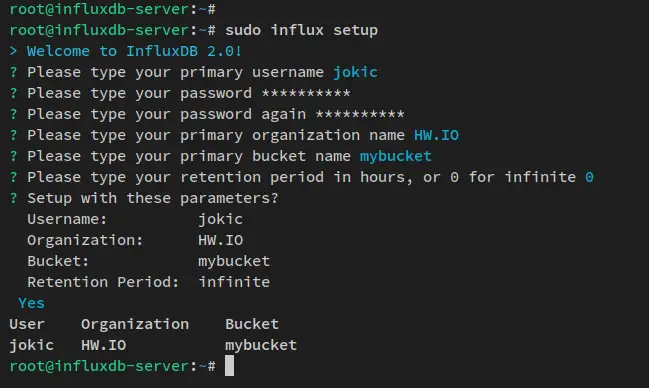
sudo influx setup
Now you will be asked for some configuration of influxdb. Input the username and password for your influxdb installation. Input the default organization name and the default bucket/database.
This example on the below screenshot shows user for the influxdb installation is 'jokic' with the organization name as 'HW.IO' and the default bucket is 'mybucket'.
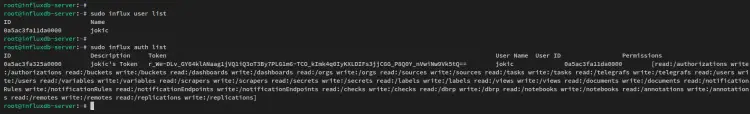
After the influxdb is configured, run the below influx command to verify the configuration.
sudo influx user list
sudo influx auth list
You'll receive an output similar to the screenshot below. The 'influx setup' command also automatically configured the token for the new admin user with some default admin permissions.
With the new admin user is created and the token generated, you'll now verify the configurations by logging in via the influxdb shell and web administration dashboard.
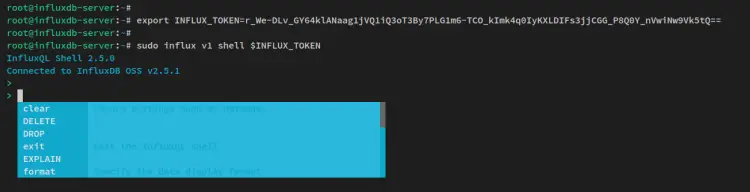
Run the below command to create a new environment variable 'INFLUX_TOKEN'. And be sure to change the token with your generated token.
export INFLUX_TOKEN=r_We-DLv_GY64klANaag1jVQ1iQ3oT3By7PLG1m6-TCO_kImk4q0IyKXLDIFs3jjCGG_P8Q0Y_nVwiNw9Vk5tQ==
Now access the influxdb shell via the influx command below.
sudo influx v1 shell $INFLUX_TOKEN
After logged in, you'll receive a message such as 'Connected to InfluxDB OSS v2.5.1'.
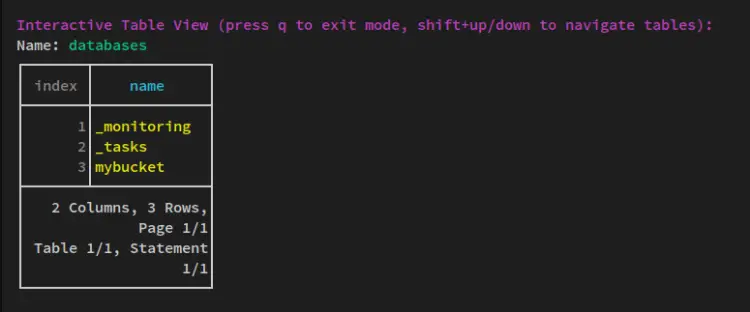
Run the following query to verify the list of buckets/databases on your inlfuxdb installation. The following terminal screen show you the bucket 'mybucket' is available on the influxdb.
show DATABASES
Now input 'q' to exit from the interactive screen. Then type 'quit' to exit from the influxdb shell.
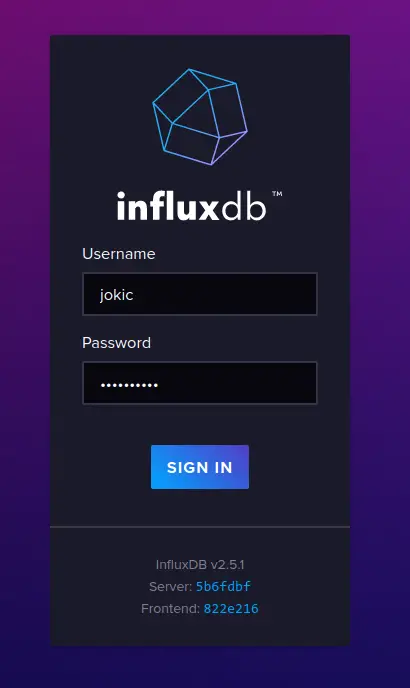
Next, open your web browser and visit your server IP address followed by the default port 8086 (i.e: http://192.168.5.8086/). You will see the influxdb login page.
Input your admin user and password and click 'SIGN IN'.
You'll now get the influxdb administration dashboard.
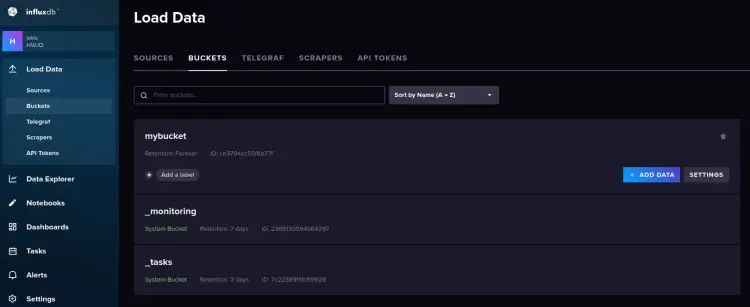
To verify the list of buckets/databases on the influxdb, click on the Load Data > Buckets, and you will see the bucket 'mybucket' is available on the influxdb.
At this point, you have installed and configured the influxdb with basic installation and configuration. You'll next secure the influxdb via SSL/TLS certificates and update the default profile for the ibnfluxdb2-cli.
Securing InfluxDB via SSL/TLS Certificates
The influxdb installation can be secured in many ways with different scenarios. You can set up authorization, and permissions for each user, and also secure transport via SSL/TLS certificates.
In this step, you'll secure the influxdb with SSL/TLS certificates, so be sure that you have generated SSL/TLS certificates before configuring the influxdb. Then, you'll update the default profile on the influxdb2-cli.
Before starting configuring, run the below command to create a new directory '/etc/influxdb/ssl' for storing SSL/TLS certificates.
mkdir -p /etc/influxdb/ssl
Copy your SSL/TLS certificate's public and private key to the new directory '/etc/influxdb/ssl'. Then, change the ownership of the SSl/TLS directory to the user 'influxdb'.
cp *.pem /etc/influxdb/ssl/
sudo chown -R influxdb: /etc/influxdb/ssl
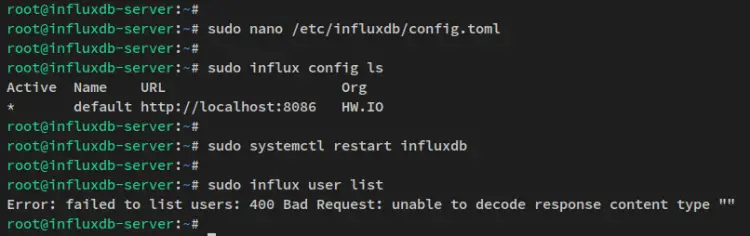
Next, open the influxdb configuration file '/opt/influxdb/config.toml' using the below nano editor command.
sudo nano /etc/influxdb/config.toml
Add the following lines, which defines the full path of SSL/TLS public and private key.
tls-cert = "/etc/influxdb/ssl/fullchain.pem"
tls-key = "/etc/influxdb/ssl/privkey.pem"
Save the file and exit the editor when you are finished.
Now run the following 'systemctl' command utility to restart the influxdb service and apply new changes.
sudo systemctl restart influxdb
With the influxdb running under the secure connection via SSL/TLS certificates, you will not be able to communicate to the influxdb via the influx command.
Run the below influx command to verify the list of profiles on the influxdb2-cli and run the query to verify the list of users on the influxdb.
sudo influx config ls
sudo influx user list
You should see an error message such as 'failed to list users: 400 Bad Request..'.
To solve the authentication issue, you must update the 'default' profile and change the default host/URL of the influxdb to the secure HTTPS connection.
Run the below command to update the 'default' profile to the secure influxdb host 'https://influxdb.howtoforge.local:8086'.
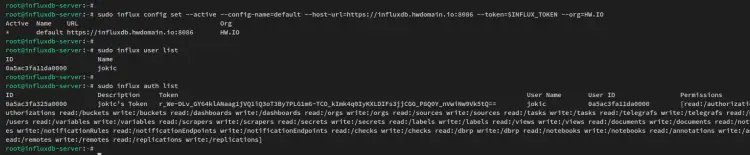
sudo influx config set --active --config-name=default --host-url=https://influxdb.howtoforge.local:8086 --token=$INFLUX_TOKEN --org=HW.IO
Now verify the new update 'default' profile via the influx command below.
sudo influx user list
sudo influx auth list
You should now be able to communicate again with the influxdb via the influx command. And the connection between the influx command to the influxdb is secured with SSL/TLS certificates.
You now have finished the basic configuration of the influxdb server and you're ready to set up Telegraf and send system metrics to the influxdb server.
Installing and Configuring Telegraf
Telegraf is part of the time series platform created by influxdata. It's an open-source server-based agent for collecting and sending metrics and events from multiple environments such as IoT sensors, database systems, system telemetry, and DevOps tools and frameworks. Telegraf is compiled as a single binary file and written in Go, no need for external dependencies for the installation.
Telegraf is available by default on the influxdb repository. So if you're using multiple Debian servers, you must add the influxdb repository to all of your servers.
In this step, you'll install Telegraf on a Debian 11 server. Then, configure telegraf to send metrics to the influxdb server.
Run the following apt command to install telegraf on a Debian server. Be sure that the influxdb repository is added.
sudo apt install telegraf
The telegraf installation should now be running.
After telegraf is installed, run the below systemctl command utility to start the telegraf service.
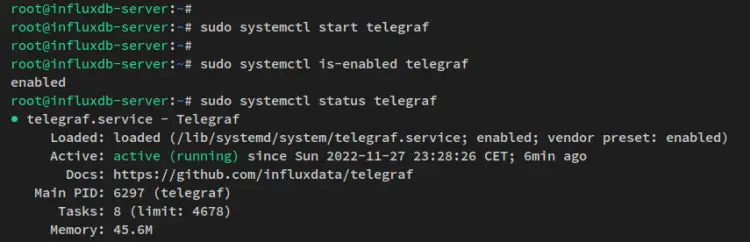
sudo systemctl start telegraf
Now verify the telegraf service using the systemctl command utility below and be sure that the service is enabled and running.
sudo systemctl is-enabled telegraf
sudo systemctl status telegraf
In your terminal screen, you'll receive the output like the following screenshot - The telegraf service is currently running and it's enabled, which means the telegeraf service will start automatically upon the bootup.
Next, open the telegraf configuration file '/etc/telegraf/telegraf.conf' using the below nano editor command.
sudo nano /etc/telegraf/telegraf.conf
Uncomment the '[[outputs.influxdb_v2]]' section and change the details configuration with the following settings. Ensure to change the influxdb URLs with a secure HTTPS connection, the token, the organization name, and the default bucket/database.
[[outputs.influxdb_v2]]
# ## The URLs of the influxdb cluster nodes.
.........
# ### ## ex: urls = ["https://us-west-2-1.aws.cloud2.influxdata.com"]
urls = ["https://influxdb.howtoforge.local:8086"]
#
# ## Token for authentication.
token = "FlIq521ZVxEA40Iz7rVVKK25sDmuEWUHm_Mbly-4mYxt-rWrYOOytVnmE5yL5bpNB_gNHBWlYXKDED9PEbk-0g=="
#
# ## Organization is the name of the organization you wish to write to.
organization = "HW.IO"
#
# ## Destination bucket to write into.
bucket = "mybucket"
Save the file and exit the editor when you are finished.
Now run the below systemctl utility command to restart the telegraf service and apply the changes.
sudo systemctl restart telegraf
With the telegraf restarted and the changes is applied, you'll next verify the telegraf installation, which you can do via the influxdb administration dashboard or via the influxdb shell.
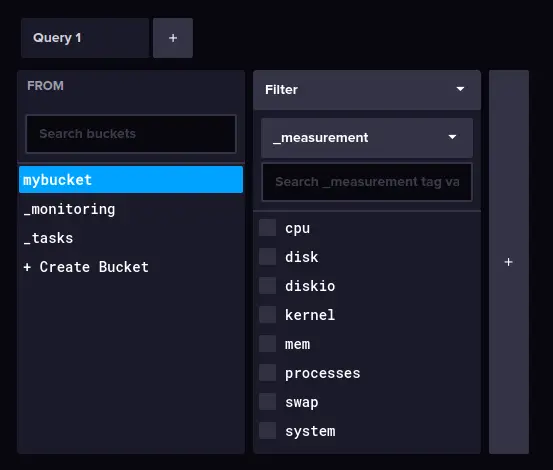
Back to the influxdb administration dashboard, click on the Data Explorer menu, and select the bucket 'mybucket'. You should see a list of telegraf metrics is available on the influxdb.
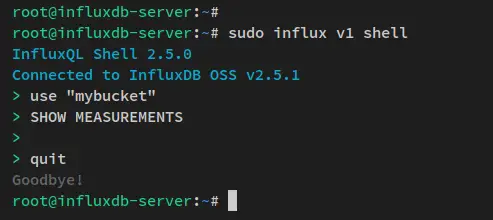
To verify from the influxdb shell, run the below command on the influxdb terminal server.
sudo influx v1 shell
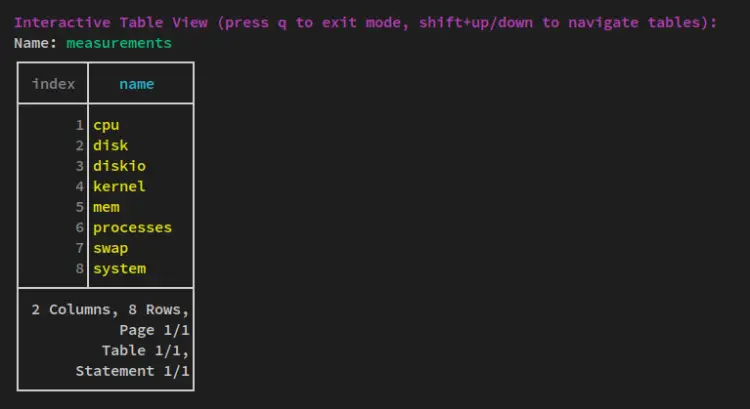
After logging in to the influxdb shell, run the following queries to verify telegraf metrics. The first query is to switch to the bucket 'mybucket', and the second query is to show available columns/measurements on the bucket.
use mybucket
SHOW MEASUREMENTS
Below is the similar output you'll receive on your terminal server - Telegraf metrics that include, the cpu, disk, diskio, kernel, mem, processes, swap, and the system is available on the influxdb server.
You have now verified that metrics from the telgeraf server is available on the influxdb server. This means that the telegraf installation and configuration is finished and successful.
In the last step, you'll learn how to create dashboard monitoring on the influxdb and set up a new monitoring system with telegraf metrics that are available on the influxdb server.
Creating Dashboard Monitoring
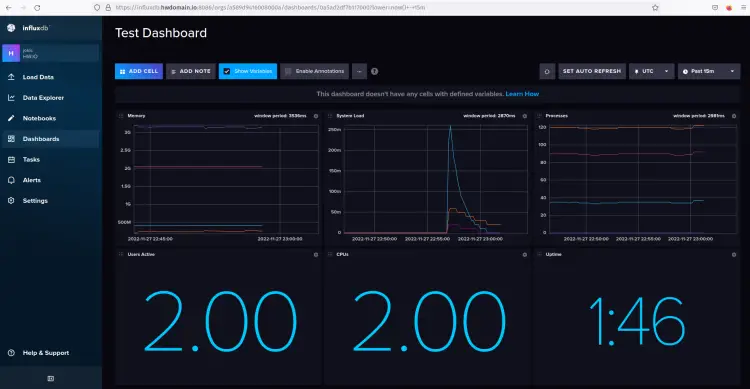
In this last step, you will set up a new dashboard for monitoring systems telemetry via the influxdb server and telegraf. You will create influxdb dashboards and set up cells for system monitoring and visualize metrics collected by the telegraf.
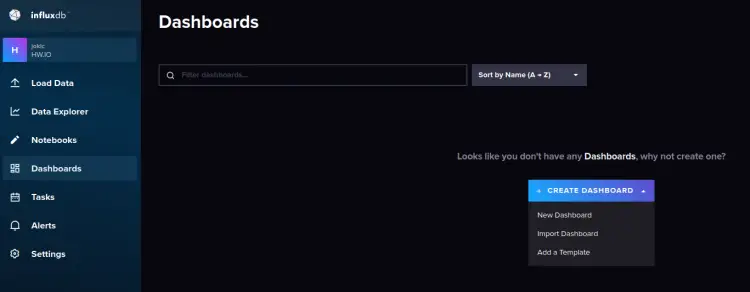
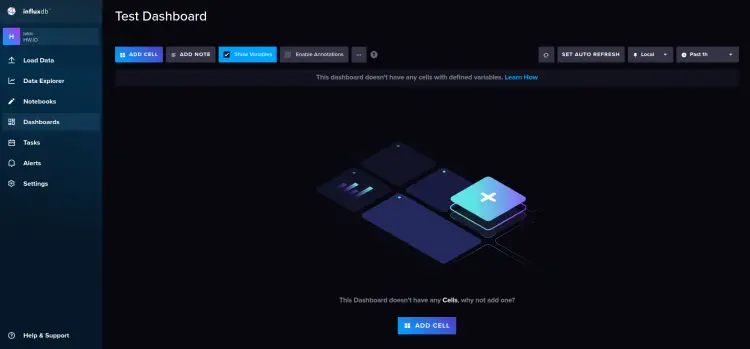
Click on the Dashboard menu, then click 'Create Dashboard'
Input the dashboard name on the top of the page, this example uses the dashboard name 'Test Dashboard'.
Now click 'ADD CELL' to add a new graph for the system monitoring.
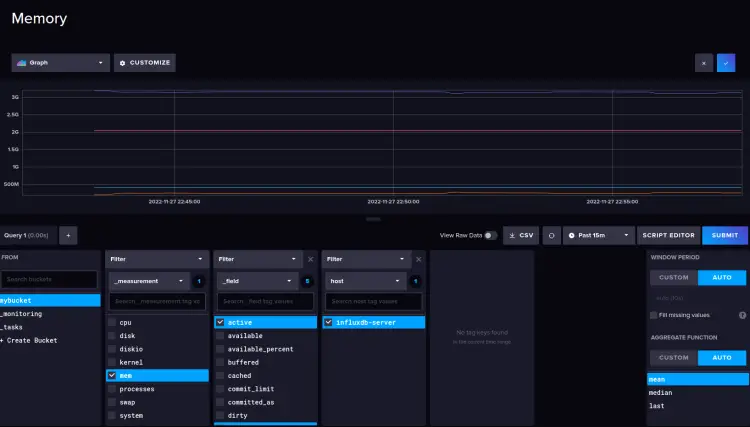
Below is the graph for memory monitoring.
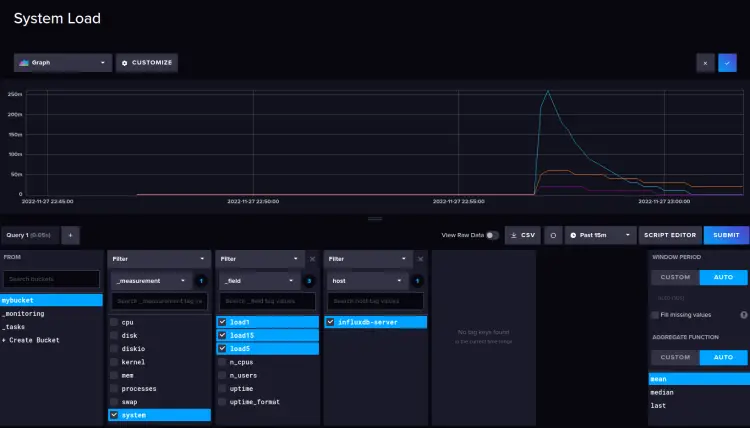
System Load monitoring.
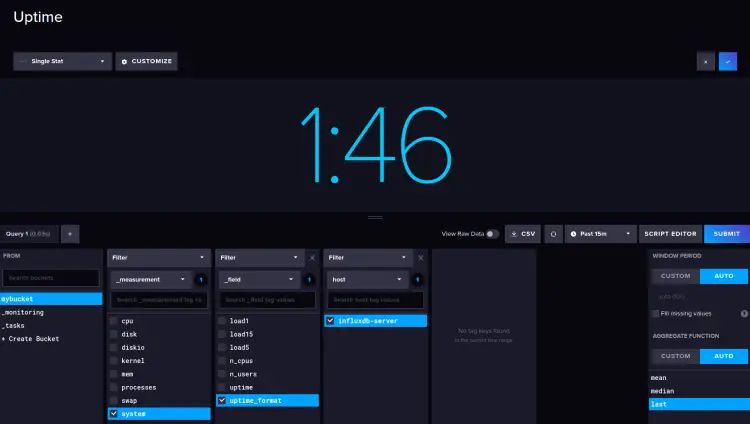
Uptime of the target server.
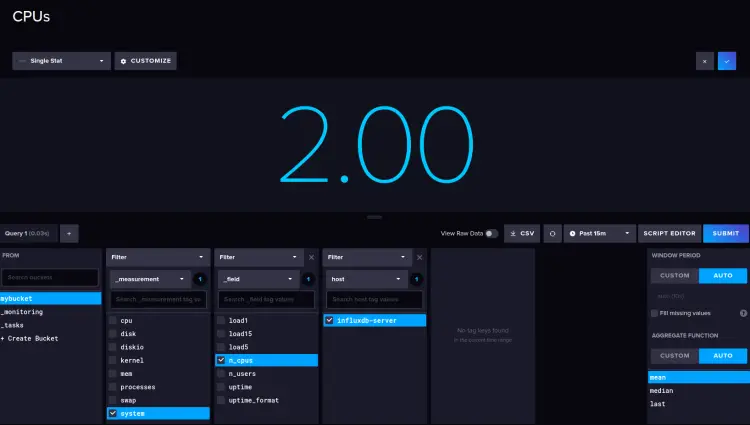
Available CPUs on the target system with the X number.
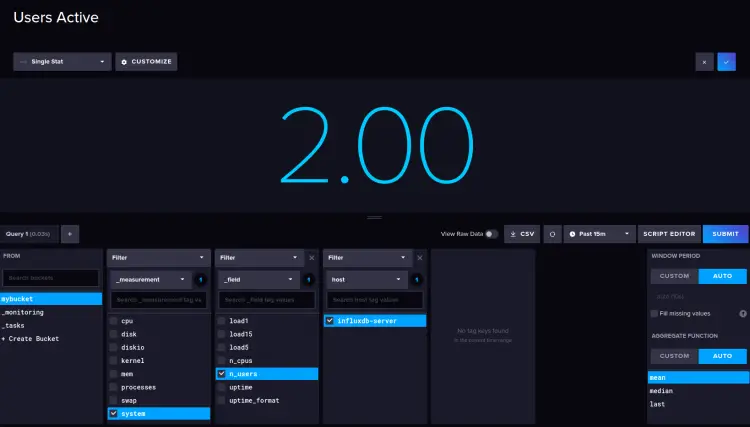
And lastly, the current user that logged on to the target machine.
After cells is created, below is the result of the example of dashboard creation on influxdb for system monitoring. All of those metrics are gathered by the telegraf and sent all metrics to the influxdb servers.
Conclusion
In this tutorial, you installed the influxdb time series database and the influxdb2-cli on a Debian 11 server. You also secured the influxdb installation with SSL/TLS certificates and configured the influxdb server via the influxdb2-cli 'influx' command line.
In addition to that, you installed and configured telegraf to collect and send metrics to the influxdb server via a secure SSL/TLS connection. And lastly, you created a dashboard for system monitoring via the influxdb server and telegraf.
With all in place, you can now visualize your systems and applications and set up the dashboard for monitoring. You can also set up influxdb tasks, set up alerting system, and more.