How to Install FreeIPA on Rocky Linux
FreeIPA is a free and open-source identity management solution for Linux/Unix operating systems. It's an upstream project from the RedHat identity Management System, which provides authentication and authorization solutions for Linux/Unix systems.
FreeIPA is built on top of multiple components, including the Directory Server, DNS, Kerberos, PKI, Certmonger, NTP Server, web administration UI, etc. It provides a centralized source of user credentials and access control. Using FreeIPA allows administrators to easily manage identity in a centralized environment, and also provides user monitoring, authentication, and access control.
In this guide, we will show you how to install the FreeIPA Identity manager on the Rocky Linux server.
Prerequisites
- A Linux server Rock Linux 8.5.
- A non-root user with sudo administrator privileges.
Setting Up FQDN
At first, you will be setting up the FQDN (Fully Qualified Domain Name) and /etc/hosts file of your Rocky Linux server.
To set up the FQDN of the server, run the below command. In this example, we are using the FQDN ipa.howtoforge.local.
sudo hostnamectl set-hostname ipa.howtoforge.local
Now edit the file /etc/hosts using nano editor.
sudo nano /etc/hosts
Input details server IP address and the FQDN of the server as below.
192.168.10.25 ipa.howtoforge.local ipa
Save the file by pressing Ctrl+x and input Y to confirm and save the file.
Next, run the following command to verify the FQDN of your Rocky Linux server.
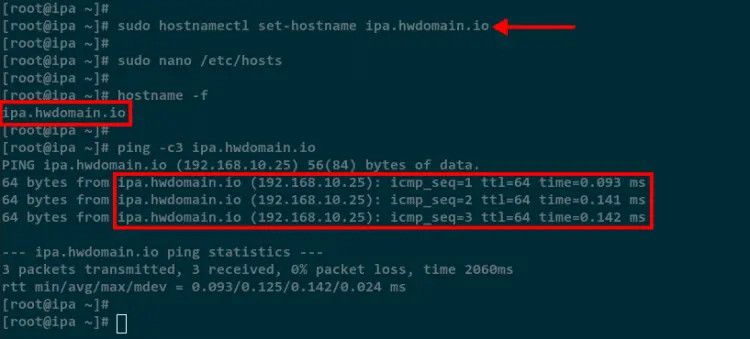
hostname -f
You should get the output of the server FQDN such as ipa.howtoforge.local.
Lastly, run the ping command below to verify the FQDN is resolved to the correct server IP address.
ping -c3 ipa.howtoforge.local
In the below screenshot, the FQDN ipa.howtoforge.local is resolved and reachable on the IP address 192.168.10.25.
Move to the next step to start the FreeIPA installation.
Installing FreeIPA Server Packages
If you have completed the FQDN and /etc/hosts file configuration, you will now be installing FreeIPA packages to the Rocky Linux system.
On the Rocky Linux system, all packages related to FreeIPA are available on the module idm:DL1. You must enable the module idm:DL1 to be able to install FreeIPA packages.
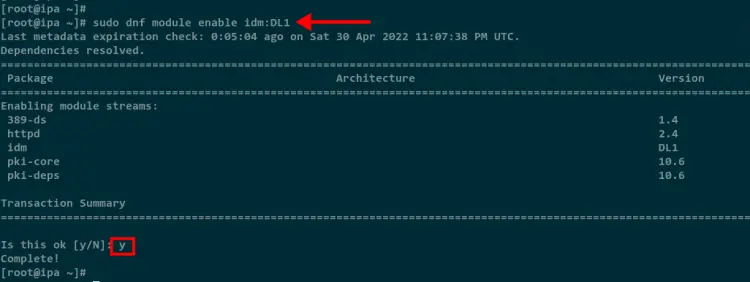
Run the following command to enable the idm:DL1 module on your Rocky Linux system.
sudo dnf module enable idm:DL1
Input Y to confirm and enable the module.
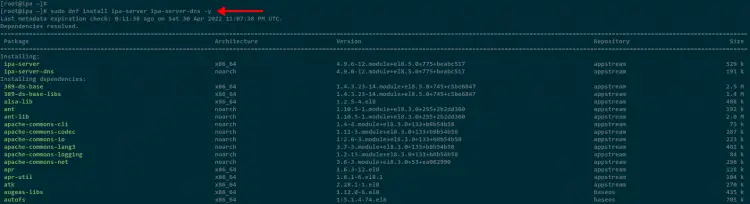
Next, install FreeIPA packages using the dnf command below. The ipa-server is the main package of FreeIPA, and the ipa-server-dns is an additional package for FreeIPA that provides DNS server functionality.
sudo dnf install ipa-server ipa-server-dns -y
Wait for all package installation, it will take time depending on your server connection.
When all installation is completed, move to the next step to start configuring the FreeIPA server.
Configuring FreeIPA Server
Now you will be setting up the FreeIPA server on the Rocky Linux system.
Before configuring the FreeIPA server, ensure the IPv6 on your server is enabled and activated. the FreeIPA server will automatically detect an error when the IPv6 is enabled on the kernel space, but not available on the network stack.
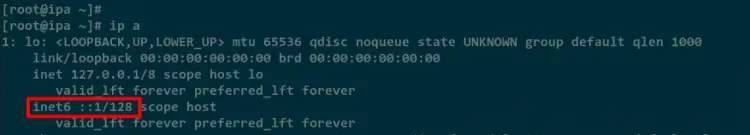
Check your server IP address to verify the IPv6 is available on your network interface.
sudo ip a
In the below screenshot, you will see the inet6 on the output, which means the IPv6 is available on the local network interface and you are ready to set up the FreeIPA server.
Next, run the ipa-server-install command below to start configuring the FreeIPA server.
sudo ipa-server-install --setup-dns --allow-zone-overlap
First, you will be shown basic information about what you will be doing to set up the FreeIPA server.
The log file for this installation can be found in /var/log/ipaserver-install.log
==============================================================================
This program will set up the IPA Server.
Version 4.9.6
This includes:
* Configure a stand-alone CA (dogtag) for certificate management
* Configure the NTP client (chronyd)
* Create and configure an instance of Directory Server
* Create and configure a Kerberos Key Distribution Center (KDC)
* Configure Apache (httpd)
* Configure DNS (bind)
* Configure SID generation
* Configure the KDC to enable PKINIT
The FreeIPA server will automatically detect the server FQDN and use it as the default server host name. Press ENTER to confirm and continue.
To accept the default shown in brackets, press the Enter key.
Enter the fully qualified domain name of the computer
on which you're setting up server software. Using the form
<hostname>.<domainname>
Example: master.example.com.
Server host name [ipa.howtoforge.local]:
Now you will need to set up the domain name for your FreeIPA server. This will automatically be detected, which is based on the server FQDN. In this example the server FQDN is ipa.howtoforge.local, so the domain name must be howtoforge.local.
Press ENTER to confirm and continue.
Warning: skipping DNS resolution of host ipa.howtoforge.local
The domain name has been determined based on the host name.
Please confirm the domain name [howtoforge.local]:
Now you will need to set up the REALM domain name for Kerberos authentication. In most cases, it's the same as the FreeIPA domain name, but with uppercase.
The kerberos protocol requires a Realm name to be defined.
This is typically the domain name converted to uppercase.
Please provide a realm name [HWDOMAIN.IO]:
Input a new password for the directory server. the password must be at least 8 characters, so be sure to use a strong password for the directory manager.
Certain directory server operations require an administrative user.
This user is referred to as the Directory Manager and has full access
to the Directory for system management tasks and will be added to the
instance of directory server created for IPA.
The password must be at least 8 characters long.
Directory Manager password:
Password (confirm):
Now input another password for the IPA admin user. This user will be used to log in to the FreeIPA server or authentication against Kerberos as an admin user. Be sure to use a strong password for your IPA admin user.
The IPA server requires an administrative user, named 'admin'.
This user is a regular system account used for IPA server administration.
IPA admin password:
Password (confirm):
In the next step, you will be asked to set up a DNS forwarder. Press ENTER to continue and the FreeIPA will automatically detect the current /etc/resolv.conf file as the DNS forwarders.
Checking DNS domain howtoforge.local., please wait ...
Do you want to configure DNS forwarders? [yes]: yes
Following DNS servers are configured in /etc/resolv.conf: 192.168.121.1
Do you want to configure these servers as DNS forwarders? [yes]:
Now you will be asked to create a reverse zone for your FreeIPA server IP address. Press ENTER to continue and the FreeIPA will automatically create a new reverse zone for your server IP address.
Do you want to search for missing reverse zones? [yes]:
Do you want to create reverse zone for IP 192.168.10.25 [yes]:
Please specify the reverse zone name [10.168.192.in-addr.arpa.]:
Using reverse zone(s) 10.168.192.in-addr.arpa.
Trust is configured but no NetBIOS domain name found, setting it now.
Enter the NetBIOS name for the IPA domain.
Only up to 15 uppercase ASCII letters, digits and dashes are allowed.
Example: EXAMPLE.
NetBIOS domain name [HWDOMAIN]:
For NTP configuration, leave it as default and press ENTER for no.
Do you want to configure chrony with NTP server or pool address? [no]:
Now you will be asked to confirm the installation and configuration of the FreeIPA server. Check again for details configurations of the FreeIPA server, then input yes and press ENTER to confirm the installation and configuration.
The IPA Master Server will be configured with:
Hostname: ipa.howtoforge.local
IP address(es): 192.168.10.25
Domain name: howtoforge.local
Realm name: HWDOMAIN.IO
The CA will be configured with:
Subject DN: CN=Certificate Authority,O=HWDOMAIN.IO
Subject base: O=HWDOMAIN.IO
Chaining: self-signed
BIND DNS server will be configured to serve IPA domain with:
Forwarders: 192.168.121.1
Forward policy: only
Reverse zone(s): 10.168.192.in-addr.arpa.
Continue to configure the system with these values? [no]: yes
Now the FreeIPA installation and configuration will be starting.
The following operations may take some minutes to complete.
Please wait until the prompt is returned.
Disabled p11-kit-proxy
Synchronizing time
No SRV records of NTP servers found and no NTP server or pool address was provided.
Using default chrony configuration.
Attempting to sync time with chronyc.
Time synchronization was successful.
Configuring directory server (dirsrv). Estimated time: 30 seconds
[1/41]: creating directory server instance
[2/41]: tune ldbm plugin
[3/41]: adding default schema
[4/41]: enabling memberof plugin
Once FreeIPA installation and configuration, you will see the following output message.
In the below output message you will also be informed about the next step for setting up the Firewall for the FreeIPA server. You will need to open some ports for the FreeIPA server, then verify the authentication using the admin user against the Kerberos server.
==============================================================================
Setup complete
Next steps:
1. You must make sure these network ports are open:
TCP Ports:
* 80, 443: HTTP/HTTPS
* 389, 636: LDAP/LDAPS
* 88, 464: kerberos
* 53: bind
UDP Ports:
* 88, 464: kerberos
* 53: bind
* 123: ntp
2. You can now obtain a Kerberos ticket using the command: 'kinit admin'
This ticket will allow you to use the IPA tools (e.g., ipa user-add)
and the web user interface.
Be sure to back up the CA certificates stored in /root/cacert.p12
These files are required to create replicas. The password for these
files is the Directory Manager password
The ipa-server-install command was successful
Now you have completed the installation and configuration of the FreeIPA server.
Setting Up Firewalld
In this step, you will be adding some services to the Firewalld rules. This includes the basic services for the FreeIPA server such as LDAP, DNS, and HTTPS.
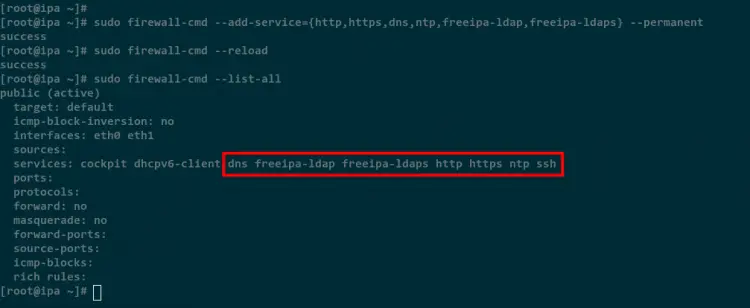
Run the firewall-cmd command below to add some services for the FreeIPA server to the Firewalld.
sudo firewall-cmd --add-service={http,https,dns,ntp,freeipa-ldap,freeipa-ldaps} --permanent
After that, reload the Firewalld rules using the below command.
sudo firewall-cmd --reload
Lastly, verify the list of rules of the Firewalld using the below command.
sudo firewall-cmd --list-all
In the below screenshot you will all services for the FreeIPA server are added to the Firewalld.
Verifying Kerberos Admin Authentication
After setting up the Firewalld, now you will verify the authentication against the Kerberos on your FreeIPA server.
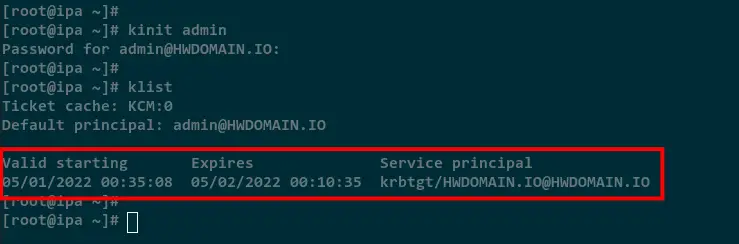
Run the below command to authenticate against the Kerberos server using the admin user.
kinit admin
Now you will be prompted for the password of your IPA server. Input the correct password.
After you are successfully authenticated, run the below command to verify the list of Kerberos tickets on your server.
klist
In the below screenshot, the new Kerberos ticket for user admin is available and the authentication against the Kerberos server is successful.
Logging in to FreeIPA Dashboard
In this step, you will be verifying the FreeIPA installation by logging in to the FreeIPA web administration dashboard.
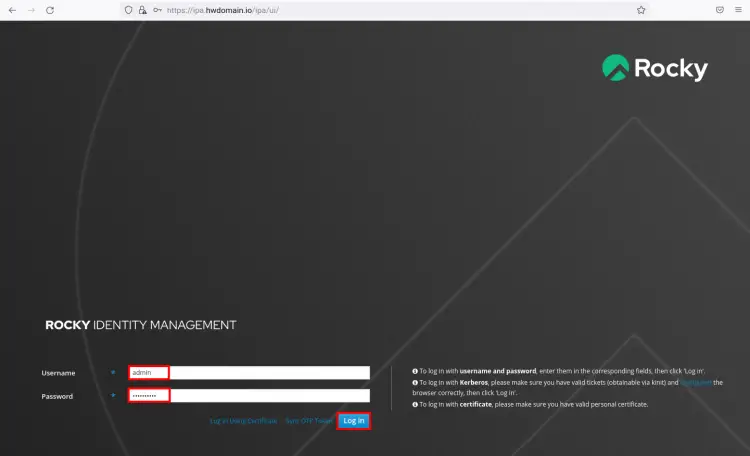
Open your web browser and visit your server IP address or FQDN as below. Now you will see the FreeIPA login page.
https://ipa.howtoforge.local/ipa/ui/
Input the FreeIPA admin user and password, then click the Log In button.
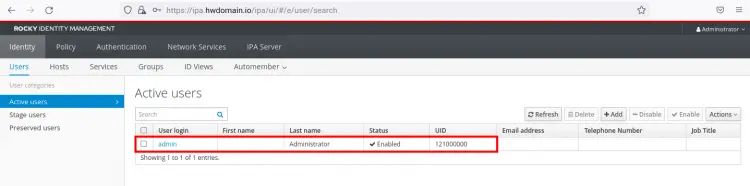
Once you have logged in, you will see the FreeIPA administration dashboard below.
Conclusion
Congratulation! You have now successfully installed and configured FreeIPA on Rocky Linux. Also, you have successfully authenticated against the Kerberos server using the IPA admin user and logged in to the FreeIPA Server.