CentOS 5 - Home Gateway Firewall With DHCP Server For Connection Sharing
Version 1.0
Author: Cameron Camp <howto [at] logicalwebhost [dot] com>
Last edited: Jan. 16th, 2008
If you're trying to set up a home network, you probably want to set up a permiter facing computer connected to your DSL/Cable modem, and then put all of your computers behind that firewall box to keep them safe. This tutorial will show you how to use a single external connection on the gateway computer (using Iptables firewall), and a second internal connection on the same box so you can connect the computers on the inside of your home/office to it, and automatically give them IP's when you hook them up (using DHCP server). Iptables can be very complicated, we will only configure a basic firewall, you can add more security later without breaking things. In Linux there are many ways to do this, this one is hopefully simple enough and will teach you the basics. I did this on a CentOS 5 box, though it would work on Debian variants with only slight modifications. During this tutorial I'm logged in as root, which you should generally NOT do, but it makes the tutorial simpler, but if you prefer to do it more securely, add "sudo" before each command and it will work.
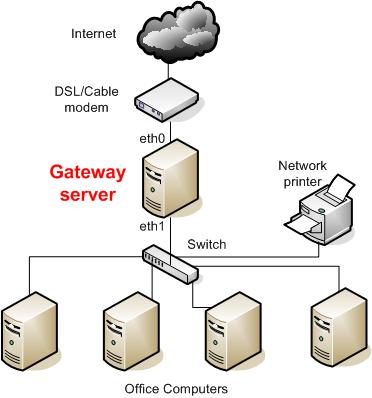
The computers on the inside of your office will also be able to talk to each other, so you can hook up printers, computers and share network connections through the switch as well. You can also set up things on your Gateway server box later like a network backup drive for all your computers using Samba relatively simply. There's a lot of expandability in this setup, but we'll keep it simple for now.
The first thing to do on your Gateway server is configure and enable Iptables, the default firewall that comes with CentOS. We will tell it to allow outbound traffic from your eth1 interface to the internet. You have to add an Iptables entry, save it and restart Iptables.
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
service iptables save
service iptables restart
Now we have to tell the kernel to start allowing forwarding so the rule will work:
echo 1 > /proc/sys/net/ipv4/ip_forward
This will only work until you reboot, so let's make it permanent, using your editor of choice, add the following line to /etc/sysconfig/network:
FORWARD_IPV4=YES
Now we have to set up a DHCP server to give out the IP's to the computers on the inside of the LAN. We do that by installing the DHCP server like this:
yum install dhcp
By default, there will be a sample DHCP file created that we'll edit and then replace the real one:
cd /usr/share/doc/dhcp-whateverversionyouhave/
vi dhcpd.conf.sample
You can cut/paste the one I'm using, or just edit yours to suit your needs. A word of caution, your network might be different than mine. This file will give your internal computers a range of IP's from 192.168.0.128 to 192.168.0.254 with a subnet mask of 255.255.255.0, change to suit your needs. You'll also have to make the IP information match on eth1 static IP later if you use your own values here.
ddns-update-style none; # keep it simple for now
ignore client-updates; # here too
DHCPARGS=eth1; # tells it what interface to listen on
subnet 192.168.0.0 netmask 255.255.255.0 {
# --- default gateway
option routers 192.168.0.1; # gateway on your eth1 internal interface
option subnet-mask 255.255.255.0; # subnet mask
option domain-name "example.com" # domain name given to client
option domain-name-servers 209.242.10.10; # the IP of your ISP's nameservers you're using
option time-offset -18000; # Eastern Standard Time - set to what you have
range 192.168.0.128 192.168.0.254; # the range of IP's your clients will get
default-lease-time 21600; # how long the client's will keep the same IP
max-lease-time 43200;
# we want the nameserver to appear at a fixed address
host ns {
next-server ns1.ispserver.net; # change to your ISP's nameservers
hardware ethernet 00:09:5B:8E:05:67; # hardware MAC
fixed-address 209.242.10.10; # your ISP's nameserver IP
}
}
Now back up your current dhcp config file and copy the one you just made over it:
mv /etc/dhcpd.conf /etc/dhcpd.conf.old
cp dhcpd.conf.sample /etc/dhcpd.conf
Now we restart the DHCP server (after checking the configuration for errors, if there are errors, you'll find them listed in /var/log/messages) so the changes will take effect
service dhcpd configtest
service dhcpd restart
Now we have to configure the eth1 (internal) interface to match what we just did in the DHCP server, so edit the file /etc/sysconfig/network-scripts/ifcfg-eth1 so it looks something like this:
DEVICE=eth1 BOOTPROTO=static ONBOOT=yes IPADDR=192.168.0.1 NETMASK=255.255.255.0 GATEWAY=10.1.10.43
You'll have to edit at least the GATEWAY IP, that's just the IP of my eth0 interface, change it be whatever your eth0 IP is, which you can find out by running:
ifconfig
It should say something like: eth0 inet addr:10.1.10.43, that's the one you want.
Next you have to tell your computer to listen for the telltale DHCP request to come across the inside network. When a client computer goes looking for a DHCP address, it sends out a blast to anyone that'll listen that has an IP address of 255.255.255.255, so you have to tell your DHCP server to listen for that IP:
route add -host 255.255.255.255 dev eth1
So now we test the setup. You should be able to go to one of the client computers, hook it up to the switch where your gateway is connected (in my case a cheap home Netgear $30 8 port switch model# FS608) and it should find an IP using your new DHCP server, and you should be able to browse the internet.
You should also set up your firewall to block more things than we've done in this tutorial to keep your internal computers safe, which you can do using the configuration tool built by running:
setup
to tell the firewall what to block. A rule of thumb is to block everything and then only allow what you need, but you can read about that elsewhere in daunting depth if you choose.

