Getting Started With Firewall Builder - Page 4
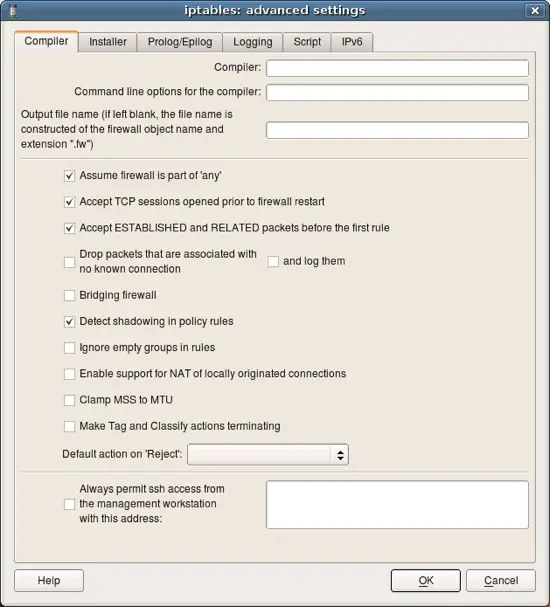
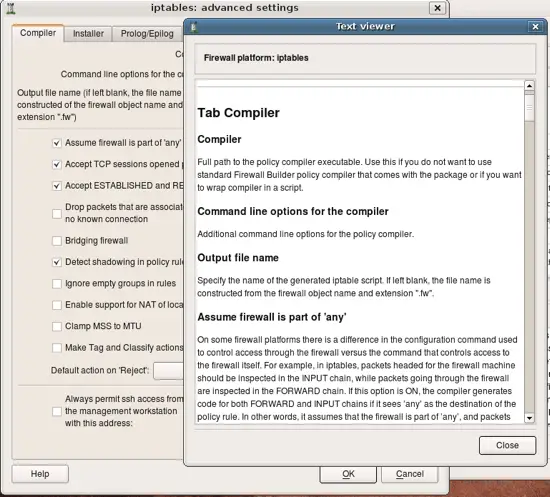
Let's inspect properties of the firewall object. Double click on the firewall "guardian" in the tree to open it in the editor panel, then click "Firewall Settings" button in the editor. This opens new dialog that looks like this. Notice button "Help" in this dialog, clicking this button opens help as shown on the next slide.
Online help explains all attributes and paramaters located in each tab of the firewall settings dialog. I enourage you to explore it as many parameters are important and affect generated iptables script in different ways.
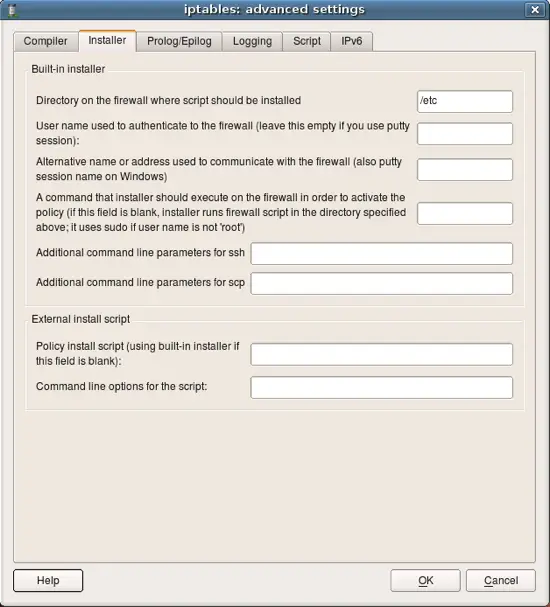
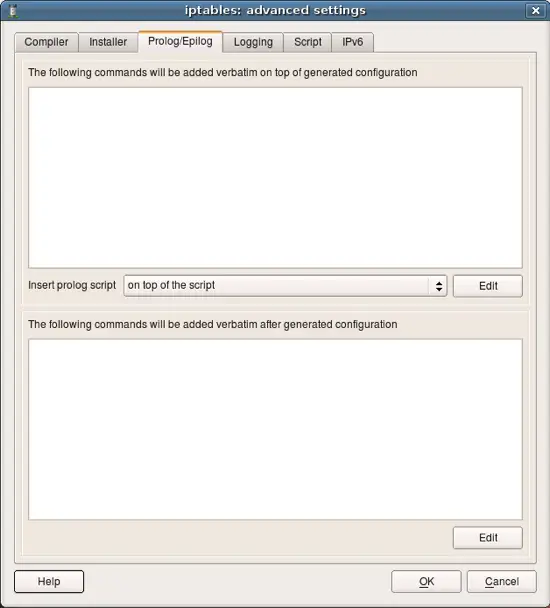
Next few screenshots show other tabs of the firewall settings dialog. You can find detailed explanations of all parameters in the online help.
This page defines various parameters for the built-in policy installer. Installer uses ssh client (pscp.exe and plink.exe on Windows) to transfer generated script to the firewall machine and activate it there.
User can define shell commands that will be included in the generated script at the beginning and in the end of it. These commands can do anything you want, such as configure some subsystems, set up routing etc.
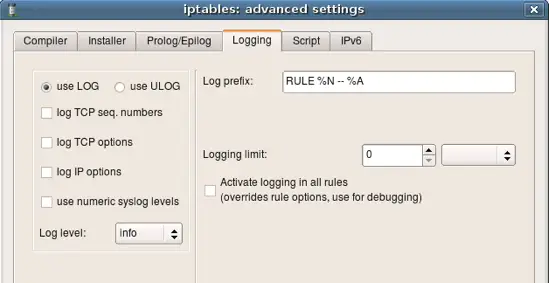
Parameters for logging.
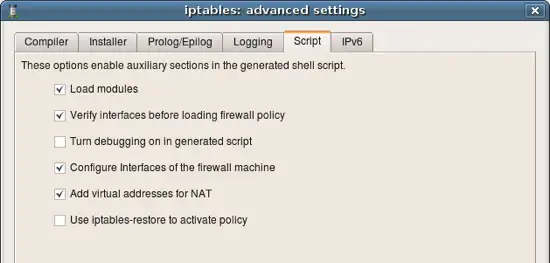
More options for the script generation. Notice that fwbuilder can produce iptables script in two formats: 1) as a shell script that calls iptables utility to add each rule one by one, or 2) it can use iptables-restore script to activate the whole policy at once. Other parameters are explained in the online help.
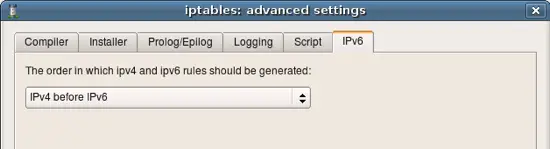
Starting with v3.0 Firewall Builder can generate both IPv4 and IPv6 policy. This tab controls the order in which they are added to the script if user defined rules for both address families in the Policy objects of the firewall.
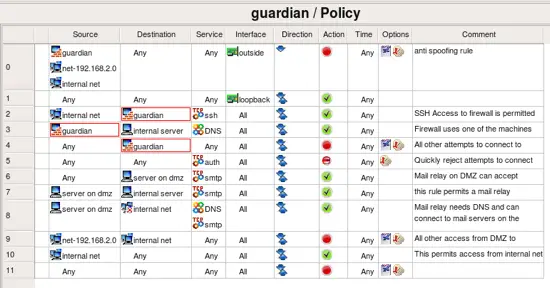
Lets take a look at the policy of the template firewall. These rules are intended to be an example, a starting point to help you create your own policy quicker. Most likely you will want to modify them to suite your requirements. Explanation of the rules given here is rather brief because the goal of this guide was only to demonstrate how to use Firewall Builder.
- Rule 0: this is an anti-spoofing rule. It block incoming packets with source address that matches addresses of the firewall or internal or DMZ networks. The rule is associated with outside interface and has direction set to "Inbound".
- Rule 1: this rule permits any packets on loopback interface. This is necessary because many services on the firewall machine communicate back to the same machine via loopback.
- Rule 2: permit ssh access from internal network to the firewall machine. Notice service object "ssh" in the column "Service". This object can be found in the Standard objects library, folder Services/TCP.
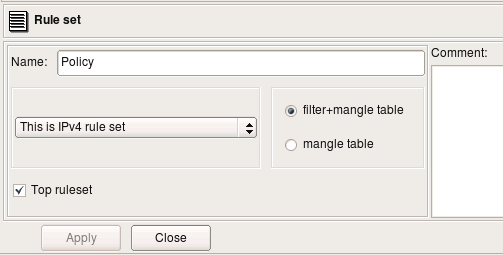
Policy rules belong to the object "Policy", which is a child object of the firewall and can be found in the tree right below it. As any other object in Firewall Builder, Policy object has some attributes that you can edit if you double click on it in the tree.
- Policy can be either IPv4, or IPv4 or combined IPv4 and IPv6. In the latter case you can use a mix of IPv4 and IPv6 addess objects in the same policy (in different rules) and Firewall Builder will automatically figure out which one is which and will sort them out.
- Policy can translate to only mangle table, or a combination of filter and mangle tables. Again, in the latter case policy compiler decides which table to use based on the rule action and service object. Some actions, such as "Tag" (translates into iptables target MARK) go into mangle table.
- "Top ruleset" means that compiler will place generated iptables rules into built-in chains INPUT/OUTPUT/FORWARD. If policy is not marked as "top ruleset", generated rules will go into user-defined chain with the name the same as the name of the policy object.
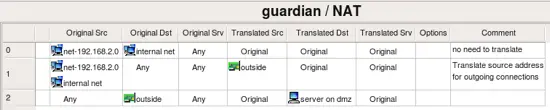
Here are preconfigured NAT rules.
- Rule 0: tells the firewall that no address translation should be done for packets coming from network 192.168.2.0 going to 192.168.1.0 (because Translated Source, Translated Destination and Translated Service are left empty)
- Rule 1: packets coming to the firewall from internal and DMZ networks should be translated so that source address will change and become that of the outside interface of the firewall.
- Rule 2: packets coming from the Internet to the interface "outside" will be translated and forwarded to the internal server on DMZ represented by the host object "server on dmz".