Protect Your Files With TrueCrypt 5 On Fedora 8
Version 1.0
Author: Oliver Meyer <o [dot] meyer [at] projektfarm [dot] de>
This document describes how to set up TrueCrypt 5 on Fedora 8. Taken from the TrueCrypt page: "TrueCrypt is a software system for establishing and maintaining an on-the-fly-encrypted volume (data storage device). On-the-fly encryption means that data are automatically encrypted or decrypted right before they are loaded or saved, without any user intervention. No data stored on an encrypted volume can be read (decrypted) without using the correct password/keyfile(s) or correct encryption keys. Entire file system is encrypted (e.g., file names, folder names, contents of every file, free space, meta data, etc)."
One important change in version 5 is that it is not longer affected by changes to the Linux kernel.
This howto is a practical guide without any warranty - it doesn't cover the theoretical backgrounds. There are many ways to set up such a system - this is the way I chose.
1 Preparation
1.1 TrueCrypt Group
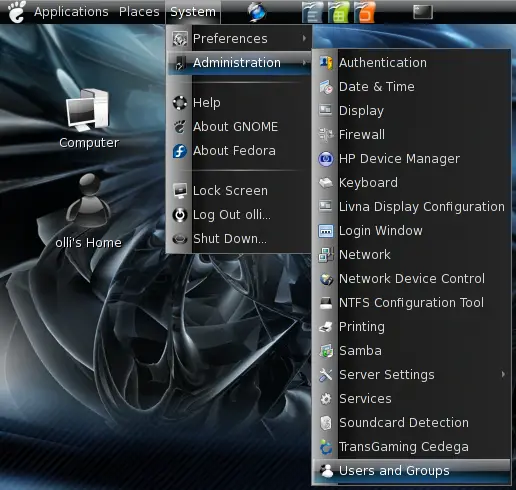
First we have to create a group that we'll use within the sudo configuration in the next step. All users that belong to this group will be able to use TrueCrypt at full volume. The settings for users and groups are available in the Gnome system menu.
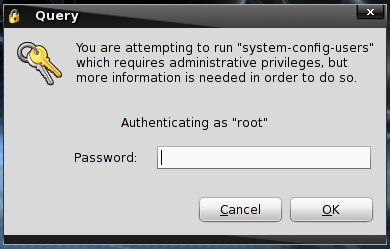
Enter the root password.
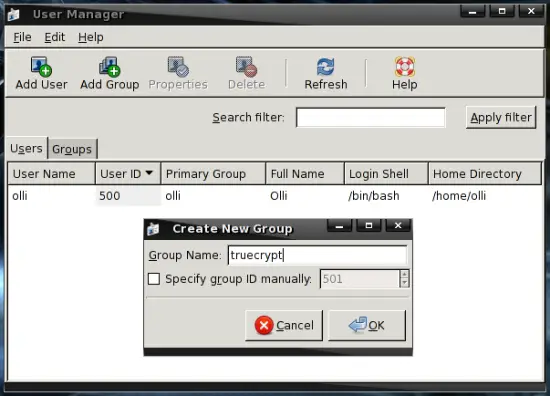
Click on "Add Group" and create the group "truecrypt".
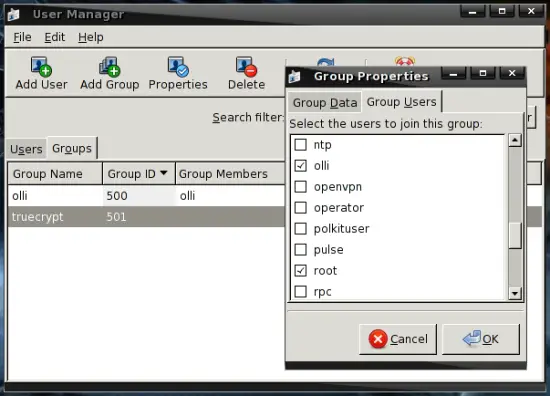
Afterwards click on the "Groups"-tab and double click on the new group "truecrypt". Click on "Group Users" in the "Group Properties" window and add root and all users that shall be able to use TrueCrypt to the group.
1.2 Sudo
Install the following package with yum or your preferred yum-frontend.
- sudo
After that we have to adjust the sudo configuration in order that all members of the group "truecrypt" are able to use it (needed to mount crypted files/devices). Open the sudo configuration (root privileges needed) via:
visudo
Add the following line ...
%truecrypt ALL=(root) NOPASSWD:/usr/bin/truecrypt
... and comment out:
Defaults requiretty
The configuration should look like this:
## Sudoers allows particular users to run various commands as ## the root user, without needing the root password. ## ## Examples are provided at the bottom of the file for collections ## of related commands, which can then be delegated out to particular ## users or groups. ## ## This file must be edited with the 'visudo' command. ## Host Aliases ## Groups of machines. You may prefer to use hostnames (perhaps using ## wildcards for entire domains) or IP addresses instead. # Host_Alias FILESERVERS = fs1, fs2 # Host_Alias MAILSERVERS = smtp, smtp2 ## User Aliases ## These aren't often necessary, as you can use regular groups ## (ie, from files, LDAP, NIS, etc) in this file - just use %groupname ## rather than USERALIAS # User_Alias ADMINS = jsmith, mikem ## Command Aliases ## These are groups of related commands... ## Networking Cmnd_Alias NETWORKING = /sbin/route, /sbin/ifconfig, /bin/ping, /sbin/dhclient, /usr/bin/net, /sbin/iptables, /usr/bin/rfcomm, /usr/bin/wvdial, /sbin/iwconfig, /sbin/mii-tool ## Installation and management of software Cmnd_Alias SOFTWARE = /bin/rpm, /usr/bin/up2date, /usr/bin/yum ## Services Cmnd_Alias SERVICES = /sbin/service, /sbin/chkconfig ## Updating the locate database Cmnd_Alias LOCATE = /usr/sbin/updatedb ## Storage Cmnd_Alias STORAGE = /sbin/fdisk, /sbin/sfdisk, /sbin/parted, /sbin/partprobe, /bin/mount, /bin/umount ## Delegating permissions Cmnd_Alias DELEGATING = /usr/sbin/visudo, /bin/chown, /bin/chmod, /bin/chgrp ## Processes Cmnd_Alias PROCESSES = /bin/nice, /bin/kill, /usr/bin/kill, /usr/bin/killall ## Drivers Cmnd_Alias DRIVERS = /sbin/modprobe # Defaults specification # # Disable "ssh hostname sudo <cmd>", because it will show the password in clear. # You have to run "ssh -t hostname sudo <cmd>". # # Defaults requiretty Defaults env_reset Defaults env_keep = "COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS" Defaults env_keep += "MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE" Defaults env_keep += "LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES" Defaults env_keep += "LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE" Defaults env_keep += "LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY" ## Next comes the main part: which users can run what software on ## which machines (the sudoers file can be shared between multiple ## systems). ## Syntax: ## ## user MACHINE=COMMANDS ## ## The COMMANDS section may have other options added to it. ## ## Allow root to run any commands anywhere root ALL=(ALL) ALL %truecrypt ALL=(root) NOPASSWD:/usr/bin/truecrypt ## Allows members of the 'sys' group to run networking, software, ## service management apps and more. # %sys ALL = NETWORKING, SOFTWARE, SERVICES, STORAGE, DELEGATING, PROCESSES, LOCATE, DRIVERS ## Allows people in group wheel to run all commands # %wheel ALL=(ALL) ALL ## Same thing without a password # %wheel ALL=(ALL) NOPASSWD: ALL ## Allows members of the users group to mount and unmount the ## cdrom as root # %users ALL=/sbin/mount /mnt/cdrom, /sbin/umount /mnt/cdrom ## Allows members of the users group to shutdown this system # %users localhost=/sbin/shutdown -h now
2 Install TrueCrypt
Please have a look at http://www.lfarkas.org/linux/packages/fedora/8/i386/ to find out which is the latest version for Fedora 8. When I was writing this howto it was version 5.1-1. Please note that there are no official packages available for Fedora 8.
cd /tmp/
wget http://www.lfarkas.org/linux/packages/fedora/8/i386/truecrypt-5.1-1.i386.rpm
yum localinstall truecrypt-5.1-1.i386.rpm --nogpgcheck
3 Gnome Menu
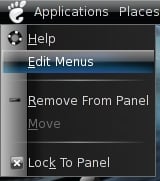
Now we create a launcher to make TrueCrypt accessible in the Gnome menu. Right click on the Gnome menu and select "Edit Menus".
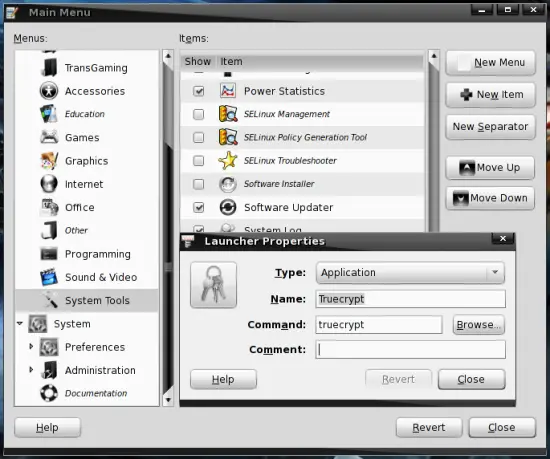
Click on a menu on the left side where you want to create the launcher (I chose "System Tools"). Afterwards click on "New Item" on the right side to create a new launcher. Set the launcher properties as follows:
Type: Application
Name: TrueCrypt
Command: truecrypt
Select a launcher icon and insert a comment if you want.
4 Access TrueCrypt
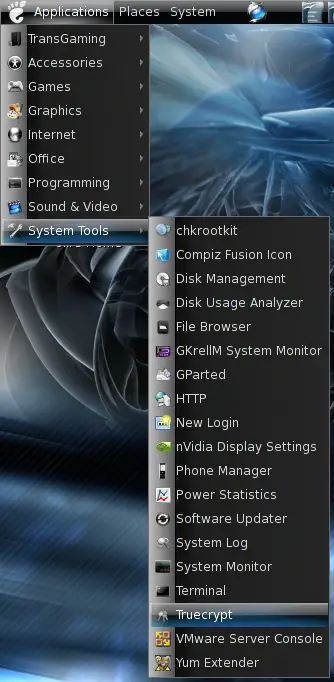
You can now use the launcher to access the TrueCrypt gui. Please note that it's also possible to use TrueCrypt via command line.
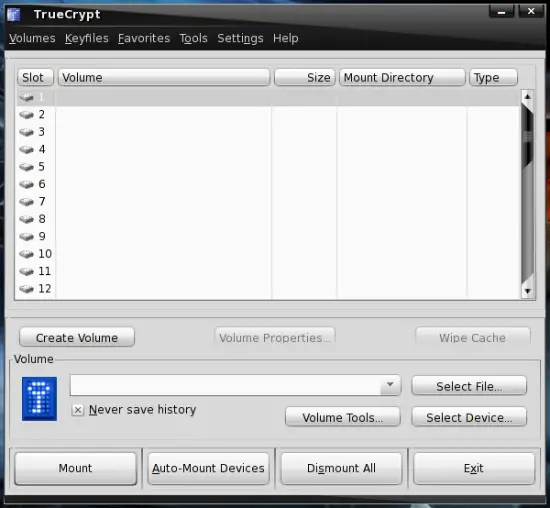
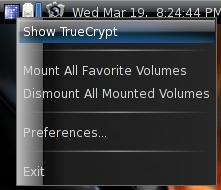
Additionally you'll see a TrueCrypt icon in the upper panel (even if you close the gui) where you can show/hide the gui, mount/dismount volumes and adjust a few settings.
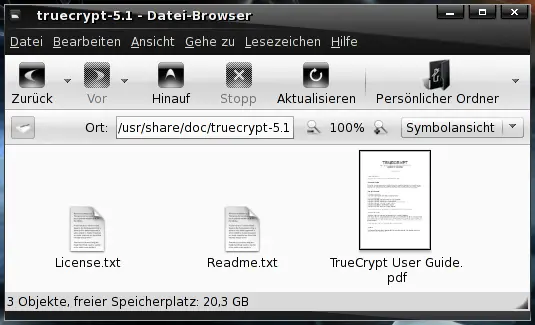
Please have a look at the documentation (/usr/share/doc/truecrypt-5.1/) to find out how to use TrueCrypt.
5 Links
- Fedora: http://fedoraproject.org/
- TrueCrypt: http://www.truecrypt.org/