Adding Two-Factor Authentication To JOSSO - Page 2
Testing the login
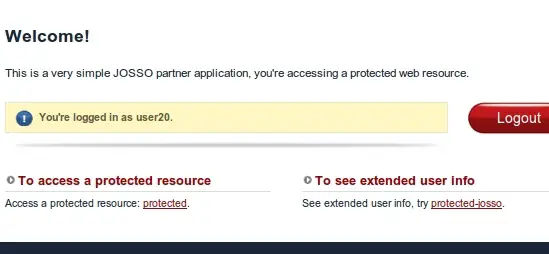
Start tomcat if you haven't and browse to http://yourserver/partnerapp. You should get this page:
Click the Login button and login with the username and password you created in JOSSO.
Adding two-factor authentication to JOSSO
Now that we know the partner app works, we can add two-factor authentication into the mix. However, before we add WiKID into JOSSO, we must first add JOSSO to WiKID. On the WiKIDAdmin web UI, click on the Network Clients tab.
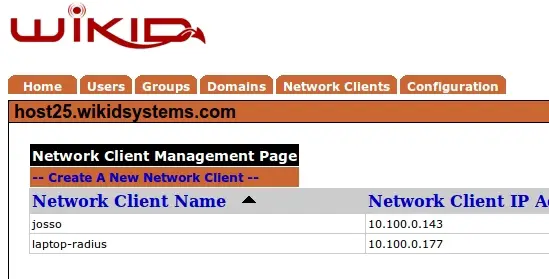
Click on Create A New Network Client. Give it a name and specify the IP address. Select WAUTH for the protocol and choose the WiKID Domain you intend to use. Then click Add.
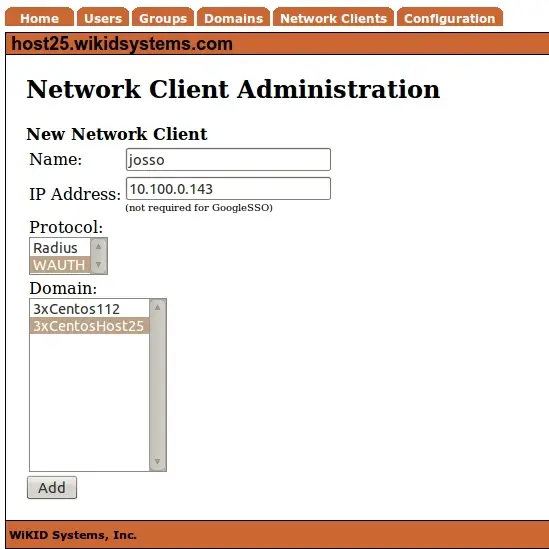
You will be prompted to create a certificate for you JOSSO server. This P12 file will identify the network client to the WiKID server and will encrypt the communications between WiKID and JOSSO (meaning this can be done over the Internet). Enter the appropriate information and hit Add NC.
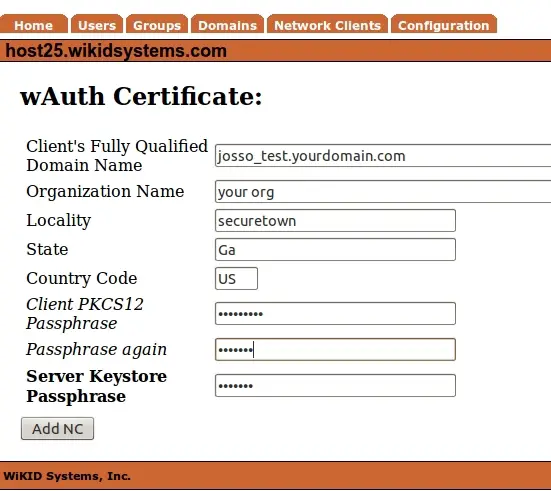
Download the created cert from the main Network Client page to your local PC. You will upload this to JOSSO. You will also have to download the CACertStore from /opt/WiKID/private.
On the palette, select Authentication and hightlight WiKID. Add it on the canvas just below the Identity Provider.
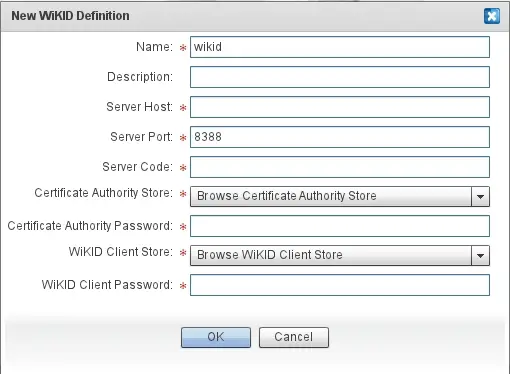
Give it a descriptive name, enter the IP address or fully qualified domain name and enter the 12 digit Domain Identifier for the Server Code. The Certificate Authority Store is the CACertStore file we downloaded earlier from /opt/WiKID/private on the WiKID server. Browse to it and upload it. The passphrase for this is the Java default: "changeit". Enter this as the Certificate Authority Password. The WiKID Client Store is the network client P12 file downloaded earlier. Choose it and then enter the passphrase for that file. Press OK.
That's all you need to do to integrate WiKID with JOSSO!
Testing the login
Now let's test the login again, this time with WIKID. Start the WiKID token, enter your PIN and request a passcode.
The OTP will automatically be copied to the clipboard. Enter your username and paste the OTP into the password box.

Once again, you should be successfully authenticated, this time with two-factor authentication.
Conclusion
Increasingly, companies are moving services to cloud providers such as Google Apps, Salesforce and SugarCRM. These services all require authentication, placing strain on users to remember strong unique passwords for each service. Clearly this is a key failure point in the security of cloud services. Single sign-on can reduce the number of credentials but creates its own "keys to the kingdom" risk. By combining two-factor authentication with SSO, everybody wins. The users get a better experience and the enterprise gets more security. In addition, WiKID's support for RADIUS means that you can also protect your VPN access.