Protect Your Files With TrueCrypt 5.1a On Debian Etch (GNOME)
Version 1.0
Author: Oliver Meyer <o [dot] meyer [at] projektfarm [dot] de>
This document describes how to set up TrueCrypt 5.1a on Debian Etch (GNOME). Taken from the TrueCrypt page: "TrueCrypt is a software system for establishing and maintaining an on-the-fly-encrypted volume (data storage device). On-the-fly encryption means that data are automatically encrypted or decrypted right before they are loaded or saved, without any user intervention. No data stored on an encrypted volume can be read (decrypted) without using the correct password/keyfile(s) or correct encryption keys. Entire file system is encrypted (e.g., file names, folder names, contents of every file, free space, meta data, etc)."
One important change in version 5 is that it is not longer affected by changes to the Linux kernel.
This howto is a practical guide without any warranty - it doesn't cover the theoretical backgrounds. There are many ways to set up such a system - this is the way I chose.
1 Preliminary Note
I used a standard Debian Etch r3 system for this howto - there were no extra repositories added.
2 Needed Packages
Let's install some needed packages (root privileges are needed).
apt-get install build-essential libfuse-dev fuse-utils pkg-config libgtk2.0-dev
3 FUSE Kernel Module
Now we have to load the FUSE kernel module (root privileges needed):
modprobe fuse
To make sure that the FUSE kernel module will be loaded automatically on boot you have to add it to the modules list (root privileges needed).
vi /etc/modules
Add the following two lines to the file.
#FUSE for TrueCrypt
fuse
4 WxWidgets
The wxWidgets source code is needed to build the TrueCrypt executable - so let's download it (do this as user, not as root!).
cd ~/Desktop/
wget http://kent.dl.sourceforge.net/sourceforge/wxwindows/wxGTK-2.8.7.tar.gz
tar xvfz wxGTK-2.8.7.tar.gz
5 TrueCrypt
5.1 Get It
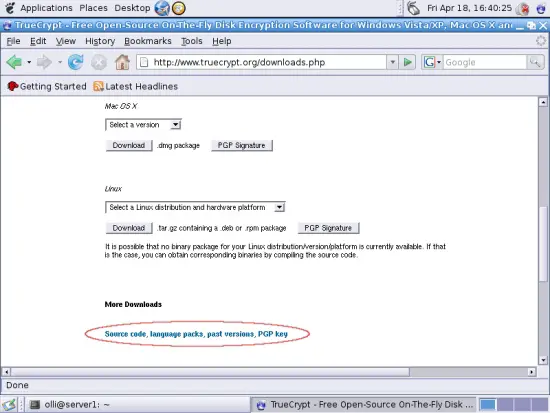
Open http://www.truecrypt.org/downloads.php within your preferred browser and click on the corresponding link to get to the download page for the source code.
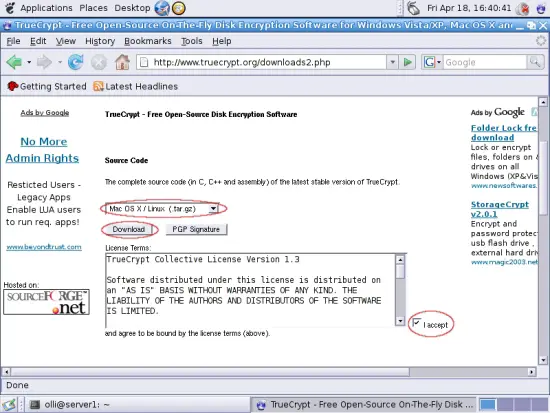
Select "Mac OS X / Linux (.tar.gz)" from the drop-down menu, read the license agreement and accept it if you agree with it. Now click on "Download" ...
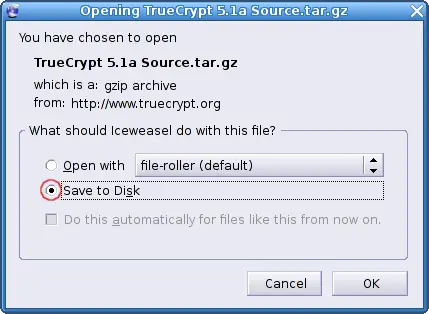
... and save the file.
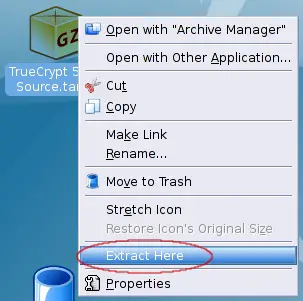
Next unpack the file. You can do this on the desktop ...
... or from the command line (do this as user, not as root!).
cd ~/Desktop/
tar xvfz TrueCrypt\ 5.1a\ Source.tar.gz
5.2 Compile It
Now we compile the TrueCrypt executable (do this as user, not as root!).
cd ~/Desktop/truecrypt-5.1a-source/
make WX_ROOT=~/Desktop/wxGTK-2.8.7 wxbuild
make
Ignore the warning "gsockgtk.cpp:134: warning: ´wxDummyGsockVar´ defined but not used" - that's nothing important.
At this point switch to the root account and copy the TrueCrypt executeable to the right place.
su -
%root_password%
cp /home/%your_username%/Desktop/truecrypt-5.1a-source/Main/truecrypt /usr/local/bin/
After that switch back to your user account, copy the user manual to the desktop and delete the remaninig .tar.gz files and the unpacked source files.
exit
cd ~/Desktop/
cp truecrypt-5.1a-source/Release/Setup\ Files/TrueCrypt\ User\ Guide.pdf ~/Desktop/
rm -Rf truecrypt-5.1a-source TrueCrypt\ 5.1a\ Source.tar.gz wxGTK-2.8.7 wxGTK-2.8.7.tar.gz