Zentyal As A Gateway: The Perfect Setup - Page 2
3.3. Failover
Zentyal Server can do failover on gateways. If one of the gateways fails it will be detected and traffic will go through the other one. This guarantees balanced Internet connection (unless both links fail at the same time).
In order to configure failover, Events module must be enabled (in Module Status). You also need to enable WAN Failover in the Events section. Finally, you should add connectivity check rules. Failover event will use them to detect broken link status (Network -> WAN Failover):
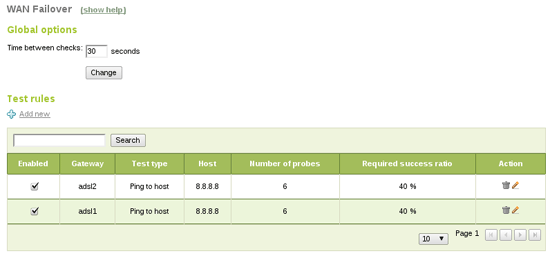
Ping to gateway checks if the gateway is up, not the Internet connection itself, ping to an external host also tests for connectivity in a fast way, DNS resolution test is a little slower but it also checks DNS resolution, and the last one, HTTP request will do a complete request to a webpage, it's more complete but also slower.
With this configuration Zentyal will ping 8.8.8.8 each 30 seconds. If two or more pings fail for a gateway it will be deactivated. If the gateway recovers it will be enabled again. None of these events will affect end users' connectivity. It's important to set up a correct time between tests, calculating max test duration times. In this case we have six ping x two gateways, which should be done in less than 30 seconds.
3.4. Basic infrastructure
In order to provide a basic infrastructure for the internal network you need to install DNS and DHCP modules using Software Management -> Zentyal Components section.
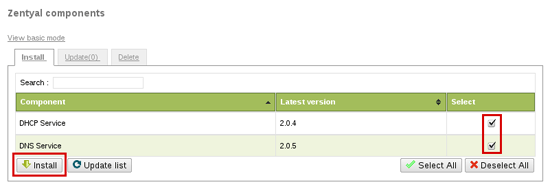
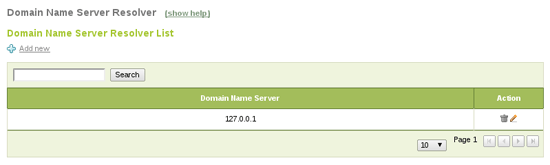
Now you have to enable these components in Module Status. DNS will act as a caching server, so you can configure Network -> DNS to 127.0.0.1 to make Zentyal use it (if you set up more than one DNS server 127.0.0.1 should be the first one):
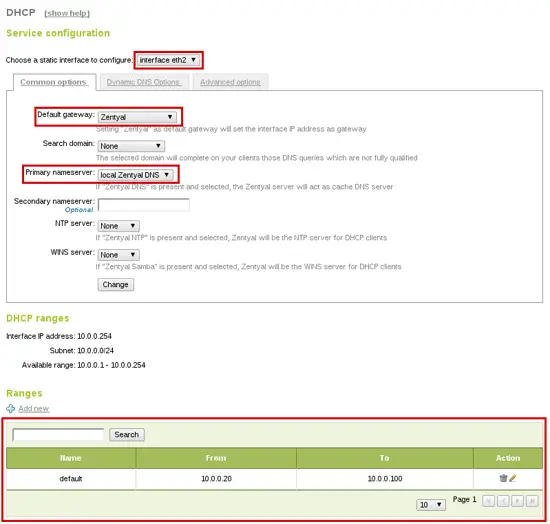
DHCP can also be configured to serve in the internal network: it will automatically configure clients to use Zentyal as a gateway and DNS. You only have to add a default range of IPs you want for the clients, 10.0.0.20-10.0.100 in this case:
4. Firewall
At this point you have a working network, with all the necessary basic networking infrastructure. Now, let's take a look to Zentyal's Firewall and how to configure it.
Zentyal is secure by default, by default firewall applies strict rules on the external interfaces and allows outgoing traffic from internal LAN. You can find the configured rules in Firewall -> Packet Filter:
- Filtering rules from internal networks to Zentyal
- Filtering rules for internal networks
- Filtering rules for traffic coming out from Zentyal
- Filtering rules from external networks to Zentyal
- Filtering rules from external networks to internal networks
- Rules added by Zentyal services (Advanced)
All these tables forbid connections by default, if you want to allow some kind of connection you need to create a new rule for this (rules are applied in order). Here are some common examples:
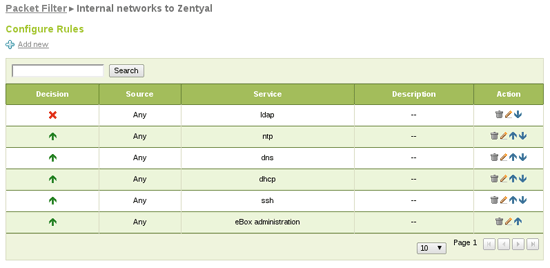
Allow internal clients to use some services except LDAP:
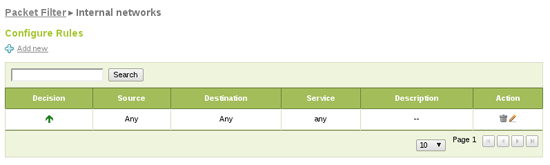
Allow all traffic from clients to the Internet:
5. HTTP Proxy
The last step of this tutorial is the HTTP Proxy setup. Zentyal's HTTP Proxy will cache users Web navigation truly decreasing bandwidth usage and it will also filter content, disallowing banned sites or content types.
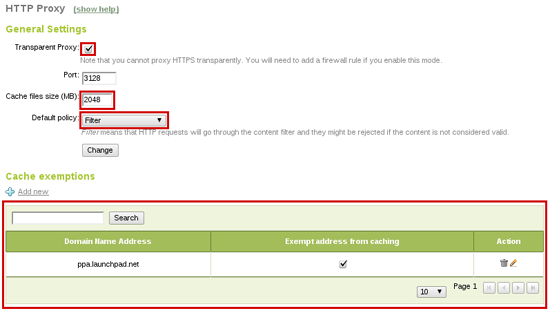
From HTTP Proxy -> General you can configure the HTTP Proxy as transparent, so clients browsers don't need to be reconfigured, HTTP requests (port 80) will automatically be redirected through the proxy. You can also increase cache size depending on your hardware and usage.
Finally, you can add a URL to cache exceptions, so the proxy will never cache it. This is useful if you need to access the webpage always in its latest version.
Setting Filter as default policy will enforce the request to go through the content filter. Now you can configure it to allow and disallow your desired pages. In HTTP Proxy -> Filter Profiles menu you will find defined filtering profiles. You can configure the default one, which will apply to all users.
In addition, here you can configure content filter threshold and add banned domain lists. Also, if you install antivirus module the proxy will use it to filter virus downloads.
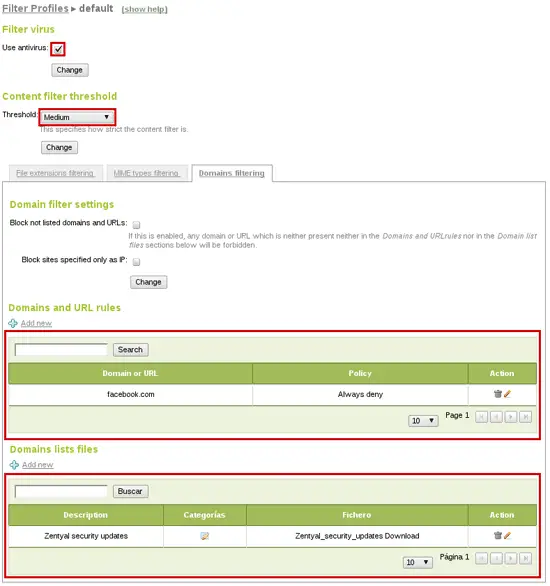
As you can see you have blocked facebook.com (just as example) but have in mind that HTTP Proxy only filters HTTP on port 80. In this case users can still reach HTTPS version of the page, so we also create a firewall rule blocking that traffic. You will need an object (Objects menu) containing facebook.com address pool:
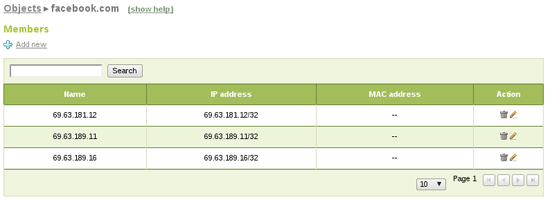
If it doesn't exist you also create a new service to match the desired traffic. In this case HTTPS (TCP with destination port 443):
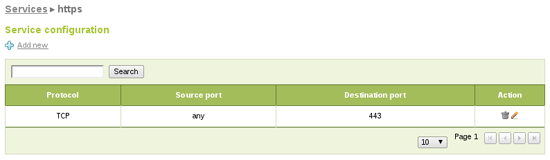
Finally you can add the firewall rule for internal networks blocking traffic matching your new object and service as destination:
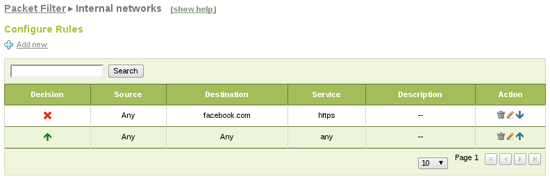
6. Conclusions
We have fully configured Zentyal Server as a gateway with load balancing, failover and HTTP proxy cache. Zentyal will be also in charge of basic infrastructure serving DHCP and DNS.
About
Zentyal, the Linux Small Business Server, offers small and medium businesses an enterprise-level, affordable and easy-to-use network infrastructure. By using Zentyal server, SMBs are able to improve the reliability and security of their computer network and to reduce their IT investments and operational costs. Zentyal server development was started in early 2004 and currently it is the open source alternative to Windows Small Business Server. Zentyal is all-in-one server that can act as a Network Gateway, Unified Threat Manager (UTM), Office Server, Infrastructure Manager, Unified Communications Server or a combination of them. Zentyal server is widely used in the small and medium businesses regardless of sector, industry or location as well as in the public administrations or in the education sector. It is estimated that there are over 50,000 active Zentyal installations all over the globe.
The author, Carlos Pérez-Aradros Herce (aka exekias), works as Zentyal Server and Zentyal Cloud developer.

